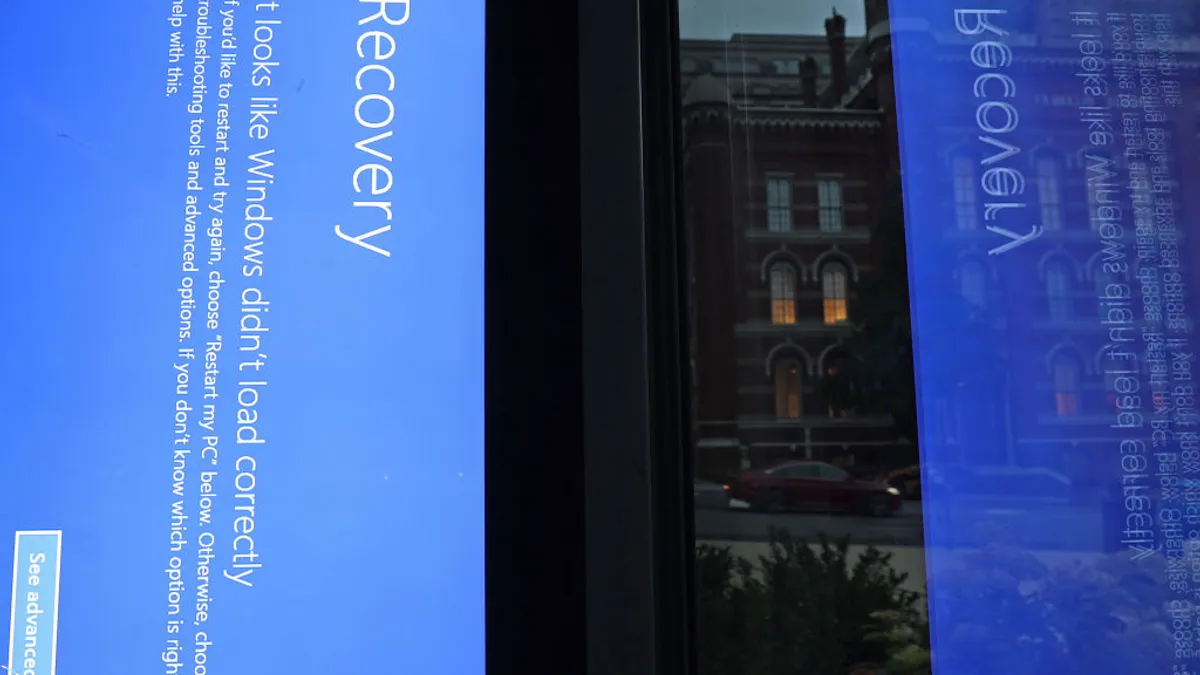
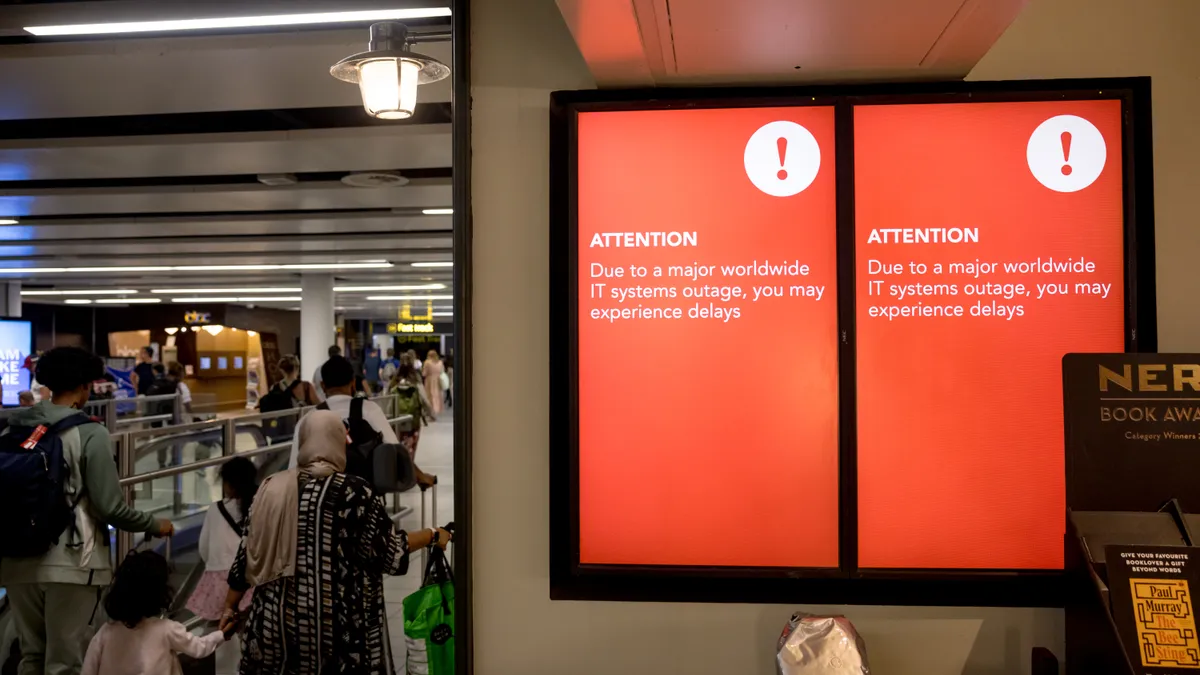
Strategy: Page 6
-
Opinion
3 tips to building a robust AI security strategy
Organizations can reap bigger benefits from AI with guardrails that combine human oversight, strong underlying security architecture and technical controls.
By Anton Chuvakin • Aug. 21, 2024 -
Palo Alto Networks CEO touts leads from CrowdStrike fallout
In the wake of the massive IT outage, some CrowdStrike customers have entered talks with Palo Alto Networks in search of a new provider.
By David Jones • Aug. 20, 2024 -
 Explore the Trendline➔
Explore the Trendline➔
 .shock via Getty Images
.shock via Getty Images Trendline
TrendlineRisk Management
An esclation of cyber risks facing businesses and government has made cyber resilience a major priority.
By Cybersecurity Dive staff -
3 CIO lessons for maximizing cybersecurity investments
Securing resources has gotten easier, said Feroz Merchhiya, City of Santa Monica CIO. But that hasn't diminished tech leaders' role in showing the value.
By Lindsey Wilkinson • Aug. 19, 2024 -
Companies aren’t as resilient against cyber risks as they think
Most companies fall short on business continuity as malicious threat activity continues to rise, a Cohesity study found.
By David Jones • Aug. 19, 2024 -
Microsoft mandates MFA for all Azure users
The company said it will require the identity and access control for all Azure sign-ins starting in October.
By Matt Kapko • Aug. 19, 2024 -
Sponsored by Tines
The biggest blockers to AI adoption, according to CISOs (and how to remove them)
74% of CISOs agree that the benefits of AI outweigh the risks. So what’s holding them back? Discover how to remove the biggest blockers to AI innovation.
By Eoin Hinchy, CEO and co-founder, Tines • Aug. 19, 2024 -
It’s time to stop thinking of threat groups as supervillains, experts say
“These villains do not have superpowers. We should not treat them like they do,” CISA Director Jen Easterly said in a keynote at Black Hat.
By Matt Kapko • Aug. 15, 2024 -
White House details $11M plan to help secure open source
National Cyber Director Harry Coker Jr., speaking at Def Con in Las Vegas, says federal assistance must be bolstered by more ownership among the community.
By David Jones • Aug. 14, 2024 -
M&A activity can amplify ransomware insurance losses, research finds
The financial severity of claims related to ransomware attacks increased more than 400% from 2022 to 2023, the study found.
By Alexei Alexis • Aug. 14, 2024 -
CISA director: Cybersecurity is ‘not an impossible problem’
In Jen Easterly's view, the solution to the industry's pains lies in secure by design. “We got ourselves into this, we have to get ourselves out,” she said during a media briefing at Black Hat.
By Matt Kapko • Aug. 13, 2024 -
Opinion
Misguided lessons from CrowdStrike outage could be disastrous
Some leaders think moving slowly is safer in light of global outages, but this approach is wrong when addressing cyber vulnerabilities and will lead to bigger problems.
By Deepak Kumar • Aug. 13, 2024 -
Microsoft Deputy CISO recounts responding to the CrowdStrike outage
The industry’s collective response to the massive outage underscored for Ann Johnson its ability to come together and put competitive interests aside.
By Matt Kapko • Aug. 12, 2024 -
CrowdStrike pursuing deal to buy patch management specialist Action1
The security firm is still working to overhaul its internal software development practices following the July 19 global IT outage involving millions of Microsoft Windows devices.
By David Jones • Aug. 9, 2024 -
LoanDepot reports net loss as cyber-related settlement hit Q2 financial results
The company disclosed $27 million in charges primarily related to a settlement deal in connection with a class action lawsuit.
By David Jones • Aug. 9, 2024 -
Delta expects $380M revenue hit due to CrowdStrike outage
The company said it canceled 7,000 flights in five days due to the IT outage, according to a Thursday filing with the Securities and Exchange Commission.
By Roberto Torres • Aug. 9, 2024 -
CrowdStrike snafu was a ‘dress rehearsal’ for critical infrastructure disruptions, CISA director says
Despite the disruption, Jen Easterly said the outage was a "useful exercise" to determine the resiliency of critical infrastructure organizations.
By Matt Kapko • Aug. 8, 2024 -

 Retrieved from J.M. Eddins Jr./U.S. Air Force.
Retrieved from J.M. Eddins Jr./U.S. Air Force. Deep Dive
Deep DiveAre cybersecurity professionals OK?
Absorbing the impacts of cyberattacks takes a personal toll on defenders. Separating the evil they see from all that’s good in the world doesn’t always come easy.
By Matt Kapko • Aug. 7, 2024 -
CrowdStrike blames mismatch in Falcon sensor update for global IT outage
The security company, in its root cause analysis report, said it is using lessons from the crash to make larger changes, while analysts predict further challenges.
By David Jones • Aug. 7, 2024 -
Microsoft joins CrowdStrike in pushing IT outage recovery responsibility back to Delta
The software provider said Delta's delayed modernization efforts were to blame for its slow recovery.
By Roberto Torres • Aug. 7, 2024 -
CrowdStrike rebukes Delta’s negligence claims in fiery letter
After the airline said it was considering legal action, CrowdStrike said Delta’s contract capped the cybersecurity provider's liability to “single-digit millions.”
By Roberto Torres • Aug. 5, 2024 -
Insured loss impact could reach $1B following CrowdStrike outage
Guy Carpenter said it could be worse: Had the incident involved a ransomware attack, losses could have reached $2 billion.
By David Jones • Aug. 5, 2024 -
After CrowdStrike outage, what will become of automatic IT updates?
Blind enterprise trust in software updates is the latest symptom of a race toward IT automation.
By Roberto Torres • Aug. 2, 2024 -
CrowdStrike outage renews supply chain concerns, federal officials say
The White House and the U.S. Government Accountability Office are raising questions about the resilience of the software supply chain and memory safety vulnerabilities.
By David Jones • Aug. 2, 2024 -
CrowdStrike investors file class action suit following global IT outage
A retirement association alleges the company misled investors about the efficacy of its software platform and quality control practices.
By David Jones • Updated Aug. 1, 2024 -
Delta grapples with $500M in CrowdStrike outage costs
Delta is rethinking how it sets up IT after its team manually reset 40,000 servers impacted by the outage, CEO Ed Bastian told CNBC Wednesday.
By Roberto Torres • Aug. 1, 2024