Strategy: Page 24
-
Microsoft rollback on macro blocking in Office sows confusion
The company said it remains "fully committed" to disabling macros by default, and the temporary measure will make the product more user friendly.
By David Jones • July 11, 2022 -
Opinion
How CISOs can prepare for new and unpredictable cyberthreats
CISOs often ask, “How do I avoid being hit by the next major cyberattack?” The problem is, that’s the wrong question.
By Jeremy D’Hoinne • July 11, 2022 -
 Explore the Trendline➔
Explore the Trendline➔
 .shock via Getty Images
.shock via Getty Images Trendline
TrendlineRisk Management
An esclation of cyber risks facing businesses and government has made cyber resilience a major priority.
By Cybersecurity Dive staff -
Mid-sized companies grapple with response to cyber crises
Limited resources, staffing and executive awareness can hamper attack response capabilities.
By David Jones • July 8, 2022 -
What to watch with 5G network security
For wireless network carriers, 5G is a model of what’s next. But it also introduces features and services that dramatically expand the threat surface.
By Matt Kapko • July 8, 2022 -
CISO priorities for the second half of 2022
Security executives from Zoom, NS1 and Oomnitza shared their security priorities for the rest of 2022, with a special emphasis on mastering the basics.
By Sue Poremba • July 5, 2022 -
Pricing pressures moderate as cyber insurance market begins to level out
A surge in new buyers has begun to offset years of rising claims and higher premiums, according to data from global insurance firm Marsh.
By Naomi Eide • July 1, 2022 -
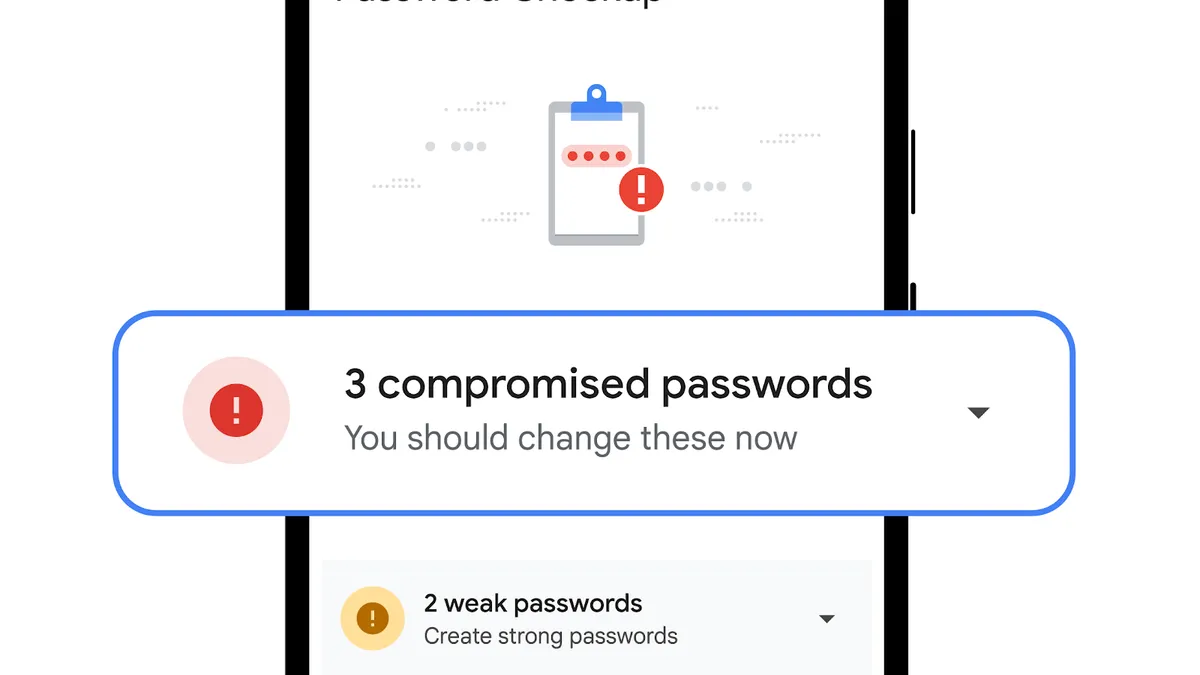
Google enhances password manager to boost security across platforms
Updates will allow users to manage passwords across platforms, including Chrome, Android and iOS.
By David Jones • June 30, 2022 -
Organizations lag on confidence and policies to manage open source security
It's taking longer for companies to find open source vulnerabilities, and shaky policies mean only the most critical vulnerabilities are attended to.
By David Jones • June 24, 2022 -
Analysts nudge businesses to decentralize cybersecurity leadership
The push is to enable employees to make informed security decisions while meeting enterprise needs with spread out security leadership.
By Lindsey Wilkinson • June 22, 2022 -
Q&A
What enterprise leaders can divine from software bills of materials
Cyber defense tool: Software bills of materials (SBOMs) can expose elements of risks in applications.
By Jen A. Miller • June 17, 2022 -
Ransomware groups shift tactics and objectives
Malware can play a major or nonexistent role in ransomware attacks. Threat actors are often only in it for the money.
By Matt Kapko • June 15, 2022 -
How and why ransomware responses go haywire
A lack of fortitude and preparation on the communications front often puts enterprises at risk for greater harm.
By Matt Kapko • June 13, 2022 -
5 takeaways from the RSA Conference
The event tried to pick up where it left off 28 months ago. Can defenders keep up with the accelerated pace and scale of the cyber threat?
By Matt Kapko • June 13, 2022 -
America's cyber chiefs have a long to-do list
The federal government wants to lead by example and communicate the urgency of the moment. First, it needs to get its security affairs in order.
By Matt Kapko • June 9, 2022 -
Threat hunters minimize Russia's cyber prowess
U.S. organizations have a lot to learn from Ukrainian cyber defenders’ sophisticated resiliency during hostile conditions.
By Matt Kapko • June 9, 2022 -
Organizational changes required to mitigate security risks
Executives are implementing new strategies to lower software supply chain risk, but evaluating internal operations could prove more effective.
By Lindsey Wilkinson • June 7, 2022 -
Oil and gas industry pledges cyber cooperation at World Economic Forum
Energy companies and industrial cybersecurity firms are working collaboratively to protect critical infrastructure in an evolving threat environment.
By David Jones • May 26, 2022 -
Feds remain in the dark as ransomware disclosure lags
The government's lack of ransomware data makes it more difficult to prevent, mitigate and recover from attacks, said Sen. Gary Peters, D-MI.
By David Jones • May 25, 2022 -
Google Cloud positions itself as a 'standalone security brand'
The platform reinforced its bid to become an all-inclusive security provider with forthcoming services for open source software and zero-trust architecture.
By Matt Kapko • May 24, 2022 -
CISOs say they're at less risk of a substantial cyberattack
A modest confidence boost and more deliberate security strategies follow two years of pandemic-induced chaos, a Proofpoint-sponsored survey found.
By Matt Kapko • May 17, 2022 -
Microsoft, Apple and Google double down on FIDO passwordless standard
The move is designed to boost digital security by allowing users to quickly authenticate across multiple devices and platforms.
By David Jones • May 5, 2022 -
M&A sets record pace as ransomware, nation-state threats fuel security demand
Enterprise customers seek consolidated, end-to-end platforms to anticipate, detect and eliminate threats.
By David Jones • April 29, 2022 -
What cyber insurance companies want from clients
Insurers evaluate how a company leverages technology and what internal standards are in place to manage risk.
By Sue Poremba • April 28, 2022 -
Ransomware attacks, payouts soared worldwide in 2021: report
More organizations are paying ransoms as attacks grow in sophistication.
By David Jones • April 27, 2022 -
IT leaders remain bullish on open source despite security hiccups
Enterprise adoption of open source has not cooled, but flaws have highlighted the need for a better understanding of dependencies.
By Brian Eastwood • April 25, 2022