Strategy: Page 23
-
CrowdStrike, Palo Alto earnings show resilience in cyber investments amid macro concerns
Enterprises are continuing to invest in cybersecurity, but remain focused on consolidating vendors.
By David Jones • Sept. 1, 2022 -
SaaS sprawl amps up security challenges amid heightened risk
Two-thirds of businesses say they're spending more on SaaS applications year over year, Axonius data shows.
By Roberto Torres • Sept. 1, 2022 -
 Explore the Trendline➔
Explore the Trendline➔
 .shock via Getty Images
.shock via Getty Images Trendline
TrendlineRisk Management
An esclation of cyber risks facing businesses and government has made cyber resilience a major priority.
By Cybersecurity Dive staff -
Multifactor authentication has its limits, but don’t blame the technology
Despite phishing attacks that evaded authentication and engulfed many technology companies of late, organizations shouldn’t hesitate to use MFA.
By Matt Kapko • Sept. 1, 2022 -
CISOs aim to balance investments, outsourcing against risks
Cyberattack risk still largely comes down to human error, regardless of how much organizations spend to bolster defense.
By Matt Kapko • Aug. 31, 2022 -
Slack enhances platform security amid rapid expansion and heightened risk
The enterprise messaging platform has faced increased customer concerns about security and privacy.
By David Jones • Aug. 31, 2022 -
Changing cyber insurance guidance from Lloyd’s reflects a market in turmoil
Rising ransomware attacks and higher payout demands have battered the insurance industry, leaving many organizations exposed and vulnerable.
By David Jones • Aug. 29, 2022 -
Tips for how to safeguard against third-party attacks
Organizations need to demand and ensure all vendors implement rigorous security measures. Sometimes the least likely tools pose the most risk.
By Matt Kapko • Aug. 25, 2022 -
Cybersecurity spending strategies in uncertain economic times
The need for strong cybersecurity programs doesn’t make it immune to cuts.
By Sue Poremba • Aug. 25, 2022 -
Risk of cyberattack emerges as top concern of US executives
A PwC study shows cyber risk is a top concern among entire C-suite and corporate boards as companies are spending additional funds to boost resilience.
By David Jones • Aug. 19, 2022 -
Google Cloud’s CISO is a short-term cyber pessimist, but a long-term optimist
Respite from seemingly omnipresent threats is hard to come by, but Phil Venables takes comfort in wins, not losses.
By Matt Kapko • Aug. 18, 2022 -
Mailchimp breach shines new light on digital identity, supply chain risk
Sophisticated threat actors are targeting weak links in the email marketing space to go after vulnerable financial targets.
By David Jones • Aug. 18, 2022 -
DigitalOcean, caught in Mailchimp security incident, drops email vendor
An attack on the email marketing firm raises questions about the continued risk of a supply chain compromise.
By David Jones • Aug. 17, 2022 -
Zero trust adoption skyrockets, nearing universal adoption
A report from Okta shows organizations fully embracing zero-trust principles, as hybrid work requires long-term changes to identity management.
By David Jones • Aug. 16, 2022 -
Don’t count on government, tech vendors to fix security woes, former CISA chief Krebs says
The state of cybersecurity is bad and it’s going to get worse, Chris Krebs said at Black Hat. But somehow things might eventually get better.
By Matt Kapko • Aug. 10, 2022 -
AWS, Splunk lead open source effort to spot and curb cyberattacks
A broad group of 18 tech companies are collaborating to establish a less cumbersome model for cybersecurity defense coordination.
By Matt Kapko • Aug. 10, 2022 -
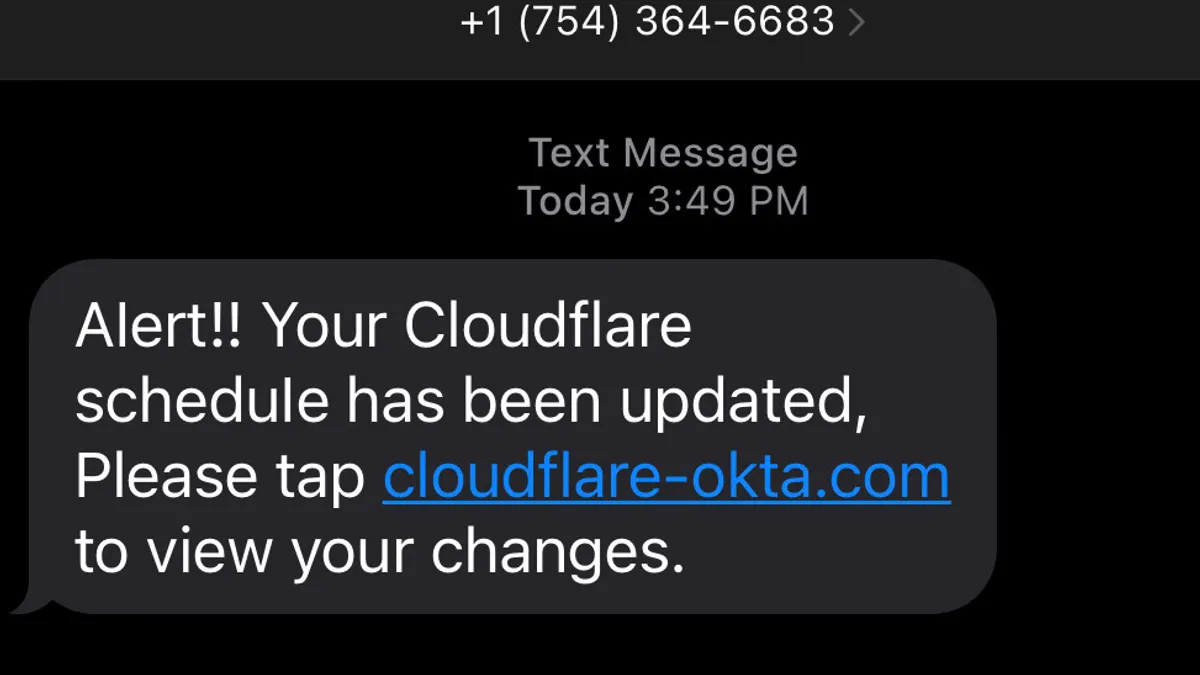
Cloudflare thwarts ‘sophisticated’ phishing attack strategy that bruised Twilio
Dissimilar responses from Cloudflare and Twilio bear important lessons in transparency, resiliency and access.
By Matt Kapko • Aug. 9, 2022 -
Encevo stays resilient post-attack, but it’s still assessing the data damage
The Luxembourg energy supplier’s ability to thwart a shutdown likely empowered its refusal to pay a ransom.
By Matt Kapko • Aug. 8, 2022 -
Ransomware defense guidance risks hang-ups under many steps
Small and mid-sized businesses don’t typically have the resources to meet every safeguard. But every action, however small, helps.
By Matt Kapko • Aug. 4, 2022 -
Threat actors shifting tactics as Microsoft blocks, unblocks and reblocks macros
Proofpoint researchers say criminal hackers are turning to container files and Windows shortcuts to distribute malware.
By David Jones • July 29, 2022 -
Mandiant red team breaches OT servers to mimic crime group techniques
Researchers are not aware of financially motivated actors using these techniques in the wild.
By David Jones • July 27, 2022 -
AWS wants to be an enterprise security strategy advisor
The cloud giant advised customers to focus on specific needs, and rely on embedded defenses running automatically behind the scenes.
By Matt Kapko • July 27, 2022 -
Sponsored by Hyperproof
SEC's cybersecurity proposals: Why visibility into risk is at the heart of it
The SEC is driving at a question every modern organization needs to consider: How should senior executives and boards manage cybersecurity risks?
July 18, 2022 -
Cyber insurers split on what’s most important in a security posture assessment
To keep up with demand, cyber insurers acknowledge the need to rethink the underwriting process, research from Panaseer shows.
By Naomi Eide • July 15, 2022 -
The US is losing the cyberspace race
Decades-old policies have failed to stem a growing threat, the Council of Foreign Relations said. What if the U.S. embraced a more limited and realistic strategy?
By Matt Kapko • July 15, 2022 -
Companies cannot see — or protect — nearly half of all device endpoints
Managing corporate devices was hard pre-pandemic. But as digital sprawl bloomed, visibility fell further behind.
By David Jones • July 13, 2022