Breaches: Page 11
-
How attackers are breaking into organizations
Threat actors lean heavily on phishing attacks, vulnerabilities in software and containers, and stolen credentials, according to top cyber vendor research.
By Matt Kapko • Aug. 15, 2022 -
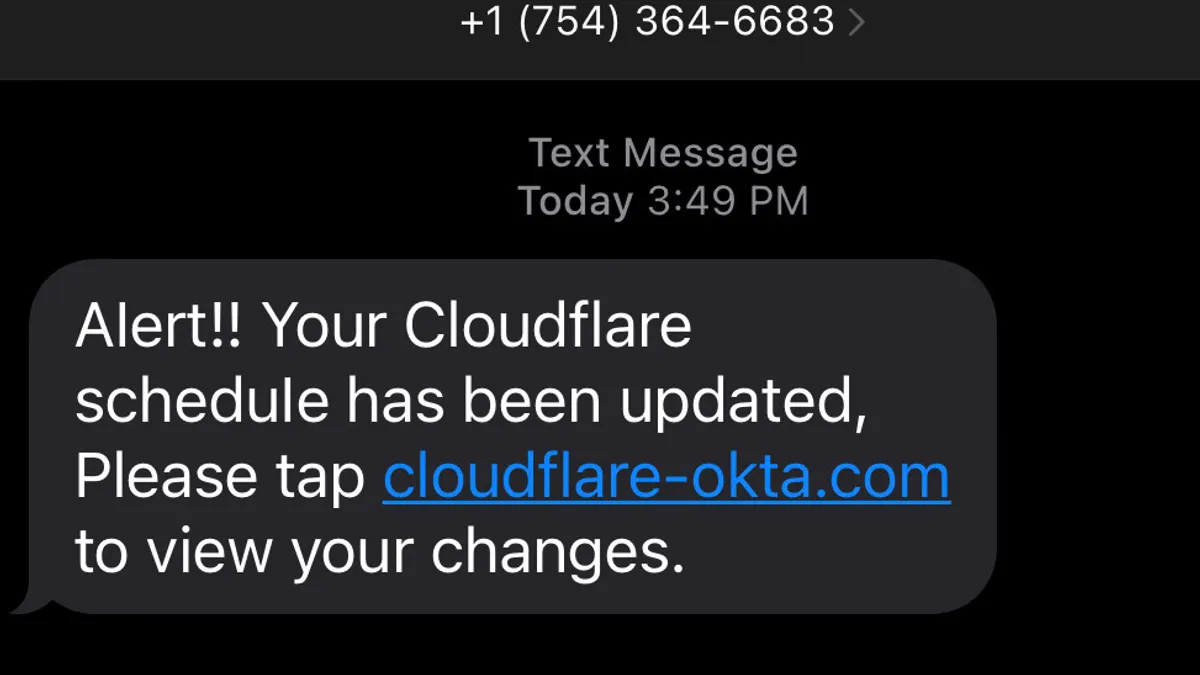
Cloudflare thwarts ‘sophisticated’ phishing attack strategy that bruised Twilio
Dissimilar responses from Cloudflare and Twilio bear important lessons in transparency, resiliency and access.
By Matt Kapko • Aug. 9, 2022 -
Hospitals have low level of accountability for connected device breaches
Only an average of 3.4% of hospitals’ IT budgets are being spent on device security, a recent survey shows.
By Rebecca Pifer • Aug. 5, 2022 -
Data breach costs spread downstream, IBM says
Nearly half of all organizations studied by IBM have minimal or no cloud security practices in place.
By Matt Kapko • July 29, 2022 -
Entrust acknowledges June cyberattack, remains tight-lipped on the details
The cybersecurity vendor has yet to disclose how the incident occurred, the type of data stolen and if ransomware was involved.
By Matt Kapko • July 28, 2022 -
Uber reaches non-prosecution deal with feds after concealing data breach
The ride-sharing firm had been under investigation by the Federal Trade Commission, when the 2016 data breach occurred, an event undisclosed until new management entered the picture.
By David Jones • July 26, 2022 -
Data breach at debt collector affects almost 2M healthcare patients
It’s the second-largest health data breach this year after the Shields Health Care Group cyberattack in March, the Department of Health and Human Services breach reporting portal shows.
By Rebecca Pifer • July 19, 2022 -
Hospital ransomware concerns rise after payment vendor breach, North Korea threats
A recently disclosed ransomware attack could have exposed patient data from more than 650 healthcare providers.
By Rebecca Pifer • July 11, 2022 -
Latest Marriott breach shows a human error pattern
The latest incident at Marriott is relatively minor compared to major breaches in late 2018 and early 2020, but it signals a pattern of neglect.
By Matt Kapko • July 7, 2022 -
Carnival to pay $5M for cyber violations to NY financial regulator
The cruise line failed to implement multifactor authentication and took 10 months to report the first of four data incidents.
By David Jones • June 27, 2022 -

 Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Attackers keep targeting VMware Horizon, exploiting unpatched Log4Shell
In one case, CISA found multiple threat actors compromising an organization using Log4Shell, which leveraged access to gain remote command and control.
By Naomi Eide • June 24, 2022 -
Breach at Flagstar Bank impacts more than 1.5M customers
The breach, which occurred between Dec. 3 and Dec. 4, is the second to impact the bank in less than two years.
By Anna Hrushka • June 22, 2022 -
Employees cause more cyber breaches in healthcare than other industries: report
Basic web application attacks, miscellaneous errors and system intrusions are at the root of the bulk of healthcare breaches, Verizon research shows.
By Rebecca Pifer • May 24, 2022 -
Tenet says 'cybersecurity incident' disrupted hospital operations
The for-profit health system has restored most critical functions, while affected facilities are starting to resume normal operations.
By Rebecca Pifer • April 27, 2022 -
Okta says 2.5% of customers breached, as Lapsus$ sows disorder
Threat researchers say Lapsus$, active on social media, revels in the spotlight. Okta's CSO called the breach screenshots "embarrassing."
By Naomi Eide • March 23, 2022 -
NYC transit worker alleges pay violations after Kronos ransomware disruption
The Metropolitan Transit Authority paid straight-time wages in a timely manner, the suit said, but it reportedly skipped overtime payments.
By Kate Tornone , Naomi Eide • Feb. 15, 2022 -
Cybersecurity outlook for 2022
Nation-state cyberthreats and Log4j have the security community on high alert; organizations need to master response and remediation.
By Naomi Eide • Feb. 14, 2022 -
Sponsored by Enzoic
In 2022, you can no longer afford to ignore credential security
Credentials are among the most sought-after targets by hackers due to the low risk and high rewards.
Jan. 31, 2022 -
NY attorney general probes widespread credential stuffing, 17 companies affected
The OAG worked with the impacted companies to uncover how threat actors bypassed security safeguards, which led almost all the companies to strengthen security controls.
By Samantha Schwartz • Jan. 6, 2022 -
Threat actor breaches HPE's Aruba Central via data repository access key
As more enterprise data moves to the cloud, security and data privacy remain paramount concerns.
By David Jones • Nov. 16, 2021 -
SolarWinds threat actor targeted IT service providers in thousands of attacks, Microsoft says
The campaign from the Russian nation-state threat actor Nobelium was caught early, but there were at least 14 compromises involving password spraying and phishing to gain access.
By Samantha Schwartz • Oct. 25, 2021 -
Ripple effects from a cyber incident take a year to develop: report
Organizations are likely to both generate and suffer the downstream consequences of cyber incidents because of the technological reliance companies have on one another.
By Samantha Schwartz • Sept. 27, 2021 -

 Carol Highsmith. (2005). "Apex Bldg." [Photo]. Retrieved from Wikimedia Commons.
Carol Highsmith. (2005). "Apex Bldg." [Photo]. Retrieved from Wikimedia Commons.
FTC warns app makers fall under breach notification rule
A breach must be reported regardless of whether it was the result of malicious action, the agency said. Any unauthorized access, including sharing information without consent, would trigger the rule.
By Shannon Muchmore • Sept. 17, 2021 -
Cybersecurity discussion growing in regulatory filings
A surge in ransomware combined with an increase in M&A activity is raising the profile of cybersecurity as a key discussion point in public filings and discussions with investors.
By David Jones • Sept. 8, 2021 -


iStock.com/pixelfit
 Sponsored by Code42
Sponsored by Code42Are you ready for the second wave of digital transformation?
In the second wave of digital transformation, understanding Insider Risk is more important than ever.
Sept. 7, 2021