Breaches: Page 10
-
7 of this year’s biggest cybersecurity stories
From vendor evolution to the long-term effects of high-profile attacks, the cybersecurity industry is rapidly evolving. Take a look at our top stories to understand just how much has changed.
By Naomi Eide • Dec. 5, 2022 -
LastPass breach fallout spreads to expose customer data
Details are scant but since the breach is a continuation from an attack on the company’s development system, “the keys to the kingdom” might be in the wrong hands, one expert said.
By Matt Kapko • Dec. 1, 2022 -
Nokia warns 5G security ‘breaches are the rule, not the exception’
A majority of 5G network operators experienced up to six cyber incidents in the past year. Defenses are especially lacking for ransomware and phishing attacks.
By Matt Kapko • Nov. 16, 2022 -
No, your CEO is not texting you
Everyone wants to stay on good terms with their employer. Threat actors know this too, and they exploit this weakness accordingly. Don’t fall for it.
By Matt Kapko • Nov. 3, 2022 -
Bed Bath & Beyond reviewing data breach
The home goods retailer doesn’t believe sensitive or personal data was accessed by the third party.
By Caroline Jansen • Nov. 2, 2022 -
U.S. Bank data breach impacts 11K customers
A third-party vendor accidentally shared the names, addresses, Social Security numbers, birthdays, closed account numbers and outstanding balances, the bank said.
By Gabrielle Saulsbery • Oct. 31, 2022 -
Sponsored by Gartner Peer Insights
Cybersecurity quarterly benchmarks: Q1, 2022
Gartner Peer Insights data and opinions run the gamut on cybersecurity maturity, budgets, and initiatives.
Oct. 24, 2022 -
As cybersecurity threats rage, colleges invest in risk prevention and pay higher insurance premiums
Cyber insurance policy renewal price increases are typically between 40% and 60%, with some increases hitting the triple digits, S&P said.
By Rick Seltzer • Oct. 14, 2022 -
CommonSpirit’s ‘IT security incident’ was likely cyberattack, security experts say
Experts view moving systems offline and interrupting access to electronic health records as a defensive move.
By Samantha Liss • Oct. 7, 2022 -
American Airlines phishing attack involved unauthorized access to Microsoft 365
The airline has begun disclosing additional details to state regulators, confirming more than 1,700 people were impacted.
By David Jones • Sept. 26, 2022 -
Morgan Stanley fined $35M by SEC over improper data disposal
The bank hired a company with no data-destruction experience to decommission hard drives and servers, which were sold to a third party and auctioned with some unencrypted customer data intact, the regulator found.
By Gabrielle Saulsbery • Sept. 21, 2022 -
Stolen single sign-on credentials for major firms available for sale on dark web
Stolen SSO credentials are available for half of the top 20 public companies, and 25% of the entire S&P 500, BitSight found.
By David Jones • Sept. 21, 2022 -
American Airlines targeted by threat actor in July data incident
The airline has notified customers about the potential release of personal data, but said there is no evidence of the data being misused.
By David Jones • Sept. 20, 2022 -
Capital One freed from consent order tied to 2019 breach
The Office of the Comptroller of the Currency determined the bank had reached a level of “safety and soundness” no longer requiring extra oversight regarding a leak of 106 million customers’ data.
By Gabrielle Saulsbery • Sept. 20, 2022 -
LastPass says it contained August breach, leaving customer data and vaults secure
After investigating alongside Mandiant, the widely used password manager has enhanced a number of security protocols in response to the four-day incident.
By David Jones • Sept. 16, 2022 -
Cloud security pros expect elevated risk for serious data breaches
Just one out of five cybersecurity and engineering professionals escaped the previous year without incident.
By Matt Kapko • Sept. 14, 2022 -
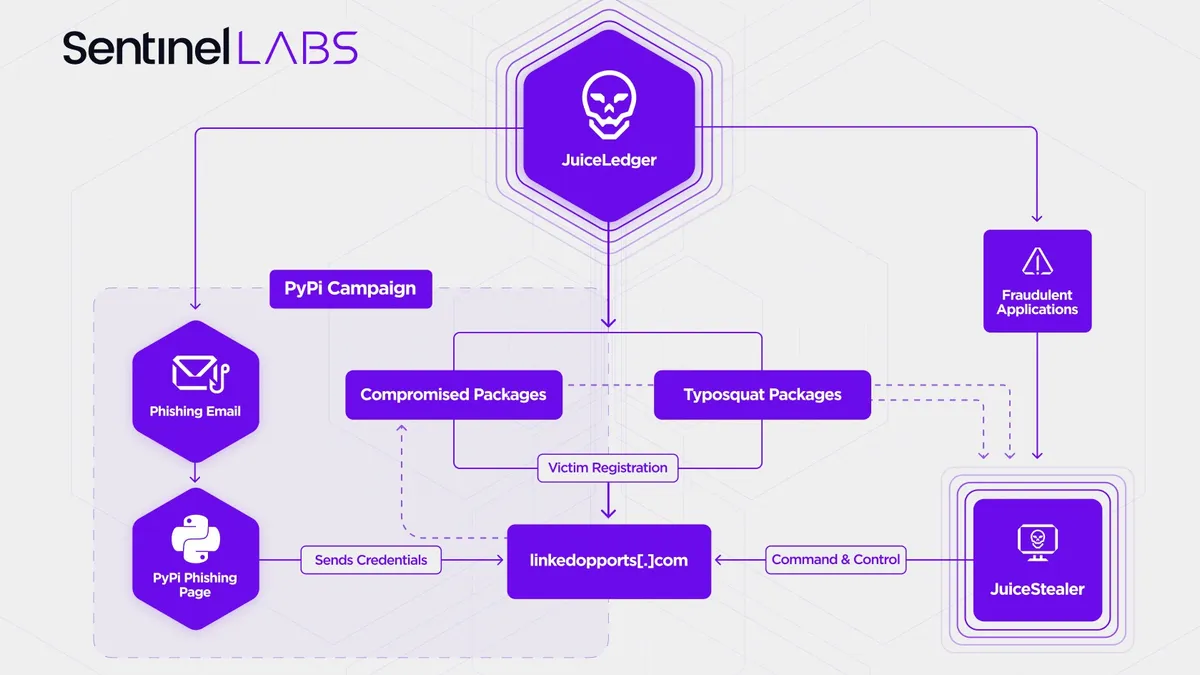
PyPI contributors targeted by JuiceLedger in latest attack against open source
The supply chain attack represents a potential risk to organizations using open source, researchers from SentinelOne and Checkmarx say.
By David Jones • Sept. 6, 2022 -
Cyberattacks pivot from large health systems to smaller hospitals, specialty clinics
The trend of attacks focusing on a systemic technology used across most providers is one that Critical Insights expects to continue this year.
By Rebecca Pifer • Aug. 29, 2022 -
Twilio discloses more victims as phishing attack effects cascade
The communications and identity authentication provider said it has discovered 163 victims thus far.
By Matt Kapko • Aug. 29, 2022 -
Almost 10K credentials compromised in phishing spree that ensnared Twilio, Mailchimp
Attackers targeted Okta identity credentials and two-factor authentication in the campaign dubbed Oktapus.
By Naomi Eide • Aug. 26, 2022 -
LastPass breached, portions of source code stolen, CEO says
The unauthorized actor did not access data or encrypted vaults from its more than 33 million registered users, however the company deployed containment and mitigation measures.
By David Jones • Aug. 26, 2022 -
Third-party attacks spike as attackers target software connections
Every third-party tool and partnership is a potential path for attack and an opportunity to exploit human behavior. The risks spread far and wide.
By Matt Kapko • Aug. 22, 2022 -
Mailchimp breach shines new light on digital identity, supply chain risk
Sophisticated threat actors are targeting weak links in the email marketing space to go after vulnerable financial targets.
By David Jones • Aug. 18, 2022 -
DigitalOcean, caught in Mailchimp security incident, drops email vendor
An attack on the email marketing firm raises questions about the continued risk of a supply chain compromise.
By David Jones • Aug. 17, 2022 -
Twilio phishing attack fallout spreads to Signal
The vendor’s widely used two-factor authentication service became a point of potential compromise for 1,900 Signal users. One user suffered a direct hit.
By Matt Kapko • Aug. 15, 2022