Threats: Page 8
-
Microsoft warns China-linked APT actor hacked US agency, other email accounts
U.S. officials alerted Microsoft about what emerged as a targeted, monthlong hacking campaign.
By David Jones • July 12, 2023 -
RomCom uses Word documents in new phishing campaign, Microsoft warns
The hackers are known to use trojanized versions of legitimate software from Adobe, SolarWinds, KeePass and others.
By David Jones • July 12, 2023 -
 Explore the Trendline➔
Explore the Trendline➔
 .shock via Getty Images
.shock via Getty Images Trendline
TrendlineRisk Management
An esclation of cyber risks facing businesses and government has made cyber resilience a major priority.
By Cybersecurity Dive staff -
JumpCloud abruptly initiates mass API key reset
The company did not specify the nature of the incident, but the sudden decision to reset all API keys could indicate something is amiss, one expert said.
By Matt Kapko • July 10, 2023 -
Threat group testing more sophisticated DDoS hacks, authorities warn
Hacktivists behind the attacks on Microsoft OneDrive and Azure are claiming recent test disruptions at Stripe, Reddit and EFTPS.
By David Jones • July 10, 2023 -
Sponsored by Elastic
Forecasts and recommendations: Elastic 2023 Global Threat Report Spring
This report summarizes threat trends, forecasts and recommendations based on analysis of millions of real-world telemetry events shared by users around the world.
By Devon Kerr • July 10, 2023 -
Hackers using TrueBot malware for phishing attacks in US, Canada, officials warn
Threat actors have been leveraging a known vulnerability in Netwrix Auditor to exfiltrate data from targeted entities since May.
By David Jones • July 7, 2023 -
Petro-Canada reports service restoration after suspected Suncor breach
The gas station chain restored card payments, but hasn’t shared specific details about the disruption. The industry has been under threat from state-linked actors.
By David Jones • June 29, 2023 -
AI linked to new crop of business email scams
Businesses can no longer count on bad spelling and grammar to red-flag problem emails: Fraudsters are using AI to craft well-written email messages at scale.
By Alexei Alexis • June 29, 2023 -
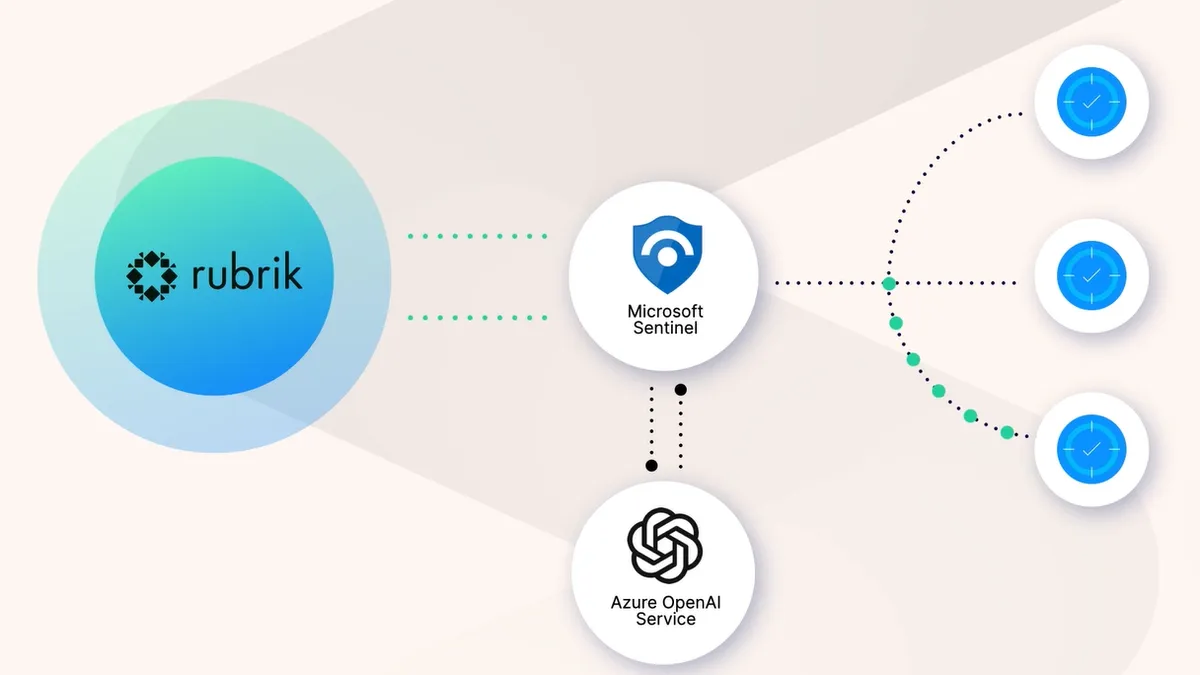
Rubrik, Microsoft partner to leverage generative AI for faster incident response
The collaboration will integrate Rubrik Security Cloud with Microsoft Sentinel and Azure OpenAI Service.
By David Jones • June 28, 2023 -
How are states supporting K-12 cybersecurity amid growing threats?
As state efforts slowly ramp up to help struggling districts, they alone can’t completely remedy cybersecurity risks, one ed tech expert said.
By Anna Merod • June 23, 2023 -
HHS warns industry about resurfaced ransomware group after attack on cancer center
In a cybersecurity notification, the department warned the sector about TimisoaraHackerTeam, or THT, after an attack on a U.S. cancer center that “significantly reduced” its capability to treat patients.
By Emily Olsen • June 21, 2023 -
Barracuda ESG devices actively exploited in broad, ongoing espionage campaign
The campaign is the broadest by a China-nexus actor since the mass exploitation of Microsoft Exchange in 2021, Mandiant researchers said.
By David Jones • Updated June 15, 2023 -
Microsoft review of Azure outage shows spike in HTTP requests as researchers blame DDoS
The Azure incident followed a series of outages in Outlook, OneDrive and other services last week. An alleged hacktivist group claimed responsibility for DDoS attacks.
By David Jones • June 14, 2023 -
Microsoft says Azure disrupted after a week of repeated service outages
The vendor is still investigating claims of DDoS attacks by a hacktivist group called Anonymous Sudan, after OneDrive, Outlook and other services were disrupted.
By David Jones • June 12, 2023 -
Microsoft investigating threat actor claims following multiple outages in 365, OneDrive
A hacktivist group known as Anonymous Sudan has claimed to be involved in DDoS attacks.
By David Jones • June 9, 2023 -
Cyber insurance market is stabilizing as growth remains certain, Moody’s says
Escalating price increases have moderated as the business has become profitable. Insurance firms are placing tight controls regarding cyber hygiene practices.
By David Jones • June 8, 2023 -
Cybercriminals target C-suite, family members with sophisticated attacks
A study by BlackCloak and Ponemon shows senior executives are being targeted for IP theft, doxxing and extortion, often through home office networks.
By David Jones • June 5, 2023 -
Moody’s cites credit risk from state-backed cyber intrusions into US critical infrastructure
Key sectors could face short-term revenue impacts and long-term reputational harm and litigation risk, the credit ratings service said.
By David Jones • May 31, 2023 -
Ahead of summer holiday weekends, IT security leaders brace for deliberate cyber mischief
Recent history shows holiday weekends and vacations provide an attack surface bonanza for threat actors.
By David Jones • May 26, 2023 -
SMBs, regional MSPs under fire from targeted phishing attacks
Sophisticated cybercriminals are attacking vulnerable target rich and resource poor organizations to reach secondary victims via phishing campaigns, Proofpoint researchers warn.
By Matt Kapko • May 24, 2023 -
BEC attacks rise as criminal hackers employ new tactics to evade detection
Threat actors are using cybercrime as a service to grow industrial strength campaigns and leveraging residential IP addresses.
By David Jones • May 23, 2023 -
Criminal actors switch tactics after Microsoft began to block macros last year
Researchers from Proofpoint have seen a rise in HTML smuggling, PDFs and OneNote files for malware delivery since late 2022.
By David Jones • May 12, 2023 -
Ransomware insurance claims jump back up
Ransomware claims filed by U.S. clients of insurance broker Marsh spiked 77% in the first quarter, following a downward trend in 2022.
By Alexei Alexis • May 10, 2023 -
CISO anxiety returns amid heightened concern of material cyberattacks
A report by Proofpoint shows a brief sense of calm about cyber has slipped away amid rising fears of economic uncertainty and insider threats.
By David Jones • May 9, 2023 -
Western Digital confirms customer data accessed by hackers in attack
The company has begun notifying customers about stolen data and expects to restore its online store next week.
By David Jones • May 8, 2023