Strategy: Page 30
-
Information sharing works, but a key obstacle awaits: reluctance
The private sector owns the majority of the attack surface. Brand-name IT and security companies have the ability, and a degree of responsibility, to contribute their expertise to national defense.
By Samantha Schwartz • March 18, 2021 -
Long-term SolarWinds consequences
SolarWinds rethinks software builds, weeds out code disparities
An attacker would have to compromise two different environments to achieve the same attack on the same code if a company has reproducibility.
By Samantha Schwartz • March 17, 2021 -
 Explore the Trendline➔
Explore the Trendline➔
 .shock via Getty Images
.shock via Getty Images Trendline
TrendlineRisk Management
An esclation of cyber risks facing businesses and government has made cyber resilience a major priority.
By Cybersecurity Dive staff -
Cloud security a shared responsibility. Where's the confusion?
The cloud meant replacing on-premise risks with a new kind risk. Some companies are unsure how to translate those responsibilities into actions.
By Samantha Schwartz • March 15, 2021 -
Federal $1.9 trillion relief bill clears path for more security, modernization funds
The appropriations in the law come as the federal government and private industry respond to two major hacks: SolarWinds and Microsoft Exchange.
By Samantha Schwartz • Updated March 11, 2021 -
White House prioritizes software security, assesses OT
"If you can't see a network quickly, you certainly don't have a prayer defending a network," said Deputy National Security Advisor Anne Neuberger.
By Samantha Schwartz • March 8, 2021 -
What OT security experts want from their IT counterparts
While IT and OT have been converging for more than a decade, the culture of cybersecurity is stuck in a silo, limiting the abilities of OT security practitioners.
By Samantha Schwartz • March 5, 2021 -
4 questions to ask after discovering a cyberattack
Identifying signs of an ongoing attack or backdoor deployment is nearly impossible for digital laggards.
By Samantha Schwartz • March 4, 2021 -
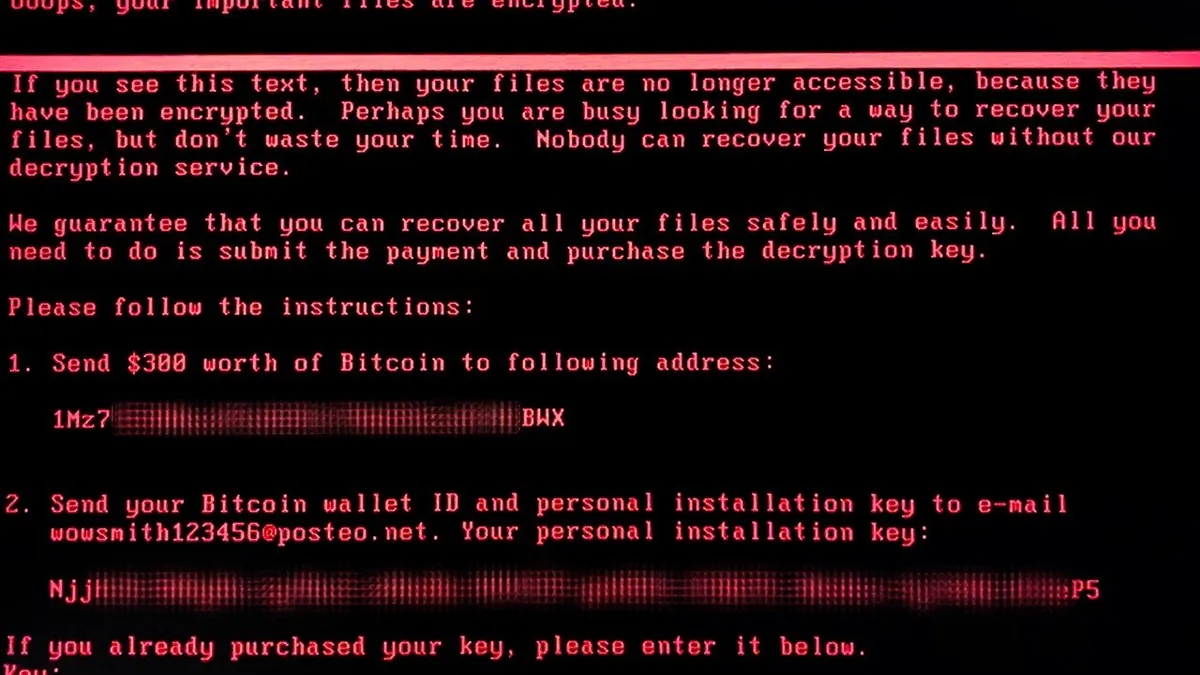
What makes ransomware a constant enterprise pain point
Threat groups mimic and manipulate the tactics, techniques and procedures of other groups, making ransomware attacks more difficult to prevent.
By Samantha Schwartz • March 3, 2021 -
Legacy tech, privacy and security issues bog down healthcare innovation
The pandemic drove hospitals and healthcare facilities to further rely on connected devices, increasing the potential for vulnerabilities in the process.
By Roberto Torres • Feb. 26, 2021 -
Businesses boost cyber budgets to improve confidence in security solutions: report
Security leaders had the least confidence in security roadmaps, security-related technology, and internal teams and skill sets, according to an Insight survey.
By Katie Malone • Feb. 25, 2021 -
How Target bridges communication gaps between threat intel analysis, detection teams
The WAVE matrix, a tool the retailer built in-house, is transferable to smaller teams with employees covering multiple security domains.
By Samantha Schwartz • Feb. 25, 2021 -
Apple faces malware threats as it makes an enterprise push
Apple made recent inroads with corporate customers and is detailing extensive security upgrades as a way of attracting the enterprise. Through it all, new techniques test the company's defenses.
By David Jones • Feb. 23, 2021 -
Long-term SolarWinds consequences
SolarWinds attack poses long-term threat of disruption, White House says
The SolarWinds hack compromised at least nine federal agencies and 100 private sector companies, said Deputy National Security Advisor Anne Neuberger in a briefing Wednesday.
By Samantha Schwartz • Feb. 18, 2021 -
Are businesses underinvesting in cybersecurity?
The issue isn't how large of a cybersecurity investment an organization makes, but rather, if it is spending funds properly.
By Sue Poremba • Feb. 16, 2021 -
Sponsored by Avanan
The next generation of email security
Now, with a single approval of an API, every line of cloud business communication can be secured.
Feb. 16, 2021 -
Sponsored by Code42
The downside of the remote work shift: 85% increase in Insider Risk
The Code42 2021 Data Exposure Report reveals a perfect storm for Insider Risk.
Feb. 16, 2021 -

 Rangel, David. [photograph]. Retrieved from https://unsplash.com/photos/4m7gmLNr3M0.
Rangel, David. [photograph]. Retrieved from https://unsplash.com/photos/4m7gmLNr3M0.
Software supply chain hacks highlight an ugly truth: The build process is broken
Software makers are coming to terms with security gaps they knew existed as the fallout from the SolarWinds hack continues.
By Samantha Schwartz • Feb. 11, 2021 -
FireEye reports record revenue in first report since Red Team hack
The company's discovery of the SolarWinds attack has fueled additional customer demand, which should be reflected in deferred revenue during 2021.
By David Jones • Feb. 3, 2021 -
Opinion
Gartner: Steps to respond to a supply chain attack
Businesses require tools to detect the lateral movement from an initial compromise and an incident response plan.
By Peter Firstbrook • Feb. 1, 2021 -
Supply chain attacks renew focus on limiting privileged access to cloud data
Supply chain attacks and rapid shifts to cloud data storage have led companies to reduce access by third-party vendors and employees to sensitive data.
By David Jones • Jan. 29, 2021 -
GDPR regulators are sinking their teeth into violators. 2020's fines are proof.
The European regulation took about a year before major fines were introduced. Watchdogs are in a grey area of harnessing better privacy standards and having zero tolerance for negligent or intentional violations.
By Samantha Schwartz • Jan. 28, 2021 -
Biden campaign cyber chief named federal CISO
Cybersecurity veterans praised the appointment, highlighting Chris DeRusha's extensive government and private sector experience, useful for navigating SolarWinds fallout.
By David Jones • Jan. 27, 2021 -

 DESIGNECOLOGIST. [Photograph]. Retrieved from Unsplash.
DESIGNECOLOGIST. [Photograph]. Retrieved from Unsplash.
Cyberthreat trends in the remote work landscape
With more workers logging in from home, companies face new cybersecurity challenges and opportunities.
By David Jones • Jan. 25, 2021 -
Cybersecurity market set to reach $60B in 2021: report
Unknown threats, like the ones emerging from the SolarWinds hack, are shaping the future of investments.
By Samantha Schwartz • Jan. 22, 2021 -
Technology's greatest supply chain challenge? Establishing trust
Geopolitics play a role in how the private sector purchases technology, influencing what on- and offshore vendors companies decide to trust.
By Samantha Schwartz • Jan. 21, 2021