Strategy: Page 18
-
3CX has a 7-part plan to shore up its security
The company is planning significant security upgrades and changes to network operations after a historic attack from a state-linked actor.
By David Jones • April 20, 2023 -
Cyber insurance premium hikes slowed in 2022, Fitch says
The deceleration was driven by a moderation of ransomware incidents and heightened levels of cyber risk awareness among corporate executives, the credit rating agency said.
By Alexei Alexis • April 18, 2023 -
 Explore the Trendline➔
Explore the Trendline➔
 .shock via Getty Images
.shock via Getty Images Trendline
TrendlineRisk Management
An esclation of cyber risks facing businesses and government has made cyber resilience a major priority.
By Cybersecurity Dive staff -
ChatGPT prompts experts to consider AI’s mark on cybersecurity
Previous AI advancements in cybersecurity tools and practices could be a precursor of what’s to come.
By Matt Kapko • April 18, 2023 -
Cyber venture capital funding slows to a trickle, a sharp decline from 2022 investment
Funding declined 58% year-over-year in Q1, though this quarter marked a slight increase from Q4 2022.
By Matt Kapko • April 14, 2023 -
Software industry leaders debate real costs and benefits of CISA security push
The global effort to promote secure by design is seen as a potential game changer for software security, but may require substantial investments and considerable cultural changes.
By David Jones • April 14, 2023 -

 Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Explore the core tactics of secure by design and default
The international joint guide encapsulates security recommendations long-touted by CISA, including technical tactics for software and infrastructure design and best practices for default security measures at large.
By Matt Kapko • April 13, 2023 -
CISA, partner agencies unveil secure by design principles in historic shift of software security
Authorities are engaging key stakeholders, but there is a broad understanding that these proposed changes will require massive changes in industry culture.
By David Jones • Updated April 13, 2023 -
CISA to unveil secure-by-design principles this week amid push for software security
The Biden administration plans to shift responsibility for product safety to the tech industry. Stakeholder discussions are already underway.
By David Jones • April 12, 2023 -
How Target approaches identity and access management
Designing an identity and access management system that provides a good user experience while preventing unauthorized access is a critical responsibility.
By Matt Kapko • April 12, 2023 -
3CX threat actor named as company focuses on security upgrades, customer retention
Mandiant attributed the supply chain attack to a North Korea-linked adversary that targeted systems using Windows-based malware.
By David Jones • April 12, 2023 -
Biden cyber officials see auto, food safety as models for security overhaul
The push to hold technology stakeholders liable for secure-by-design products will be a multiyear effort likely to involve Congress, the acting national cyber director said.
By David Jones • April 10, 2023 -
IT security leaders still told to keep data breaches quiet, study finds
Bitdefender research found 7 in 10 IT and security professionals in the U.S. have been asked to keep a breach confidential.
By David Jones • April 6, 2023 -
Experts warn against ransomware complacency
Despite reports of fewer ransomware-related cyber insurance claims and decelerating premiums in 2022, experts say the threat is still serious and evolving.
By Alexei Alexis • April 3, 2023 -
Marsh brokerage program lowers threshold for cyber insurance coverage
Cyber Pathway aims to match organizations with insurance providers and also encourage businesses to improve their controls to get better coverage.
By Matt Kapko • March 29, 2023 -
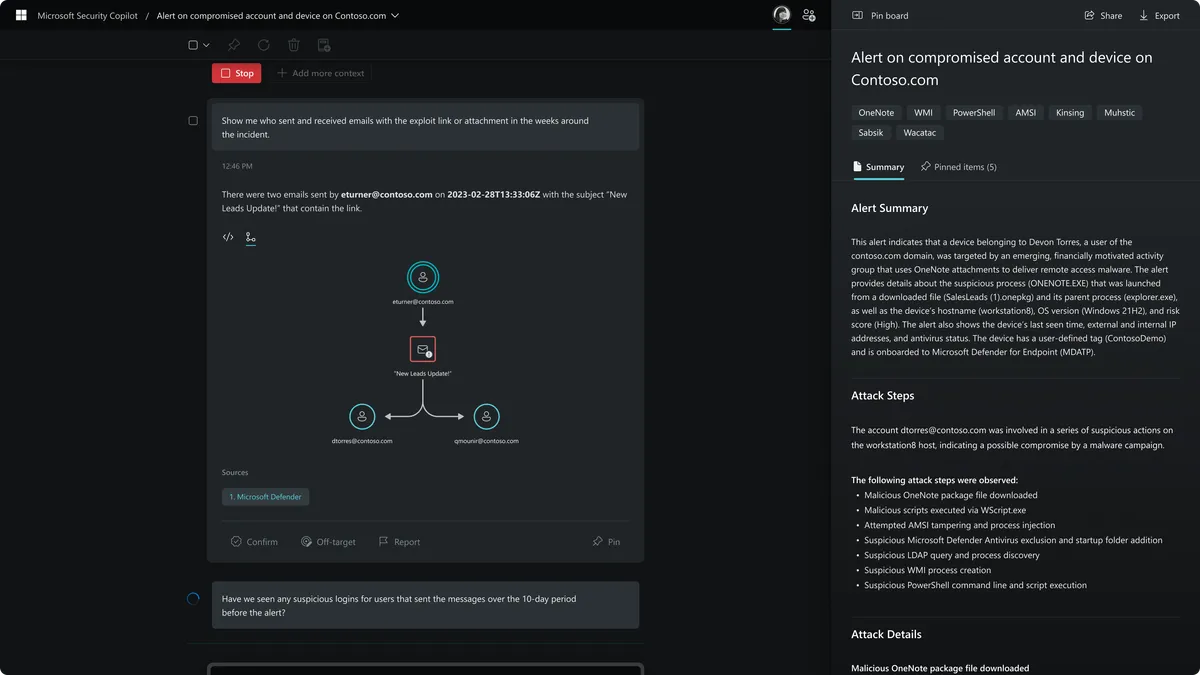
Microsoft unveils Security Copilot built on GPT-4
The technology combines the capabilities of OpenAI's generative AI with Microsoft's threat intelligence and security network.
By David Jones • March 28, 2023 -
Opinion
The proposed SEC cyber incident disclosure rule is a positive change. But it won’t make organizations safer.
If organizations want to actually get serious about protecting themselves, they need to have a robust system for handling incidents when they happen.
By Frank Shultz • March 27, 2023 -
5 steps organizations can take to counter IAM threats
Many organizations lean on identity and access management tools to perform credential management and authentication. But these systems aren’t foolproof.
By Matt Kapko • March 24, 2023 -
Threat intelligence isn’t for everyone, Google says
Most security professionals don’t have the time to read a 10-page threat intelligence report, let alone put those insights into action.
By Matt Kapko • March 23, 2023 -
Ill-prepared against cyberattacks? You’re not alone, Cisco says
The cybersecurity readiness gap looms large, and smaller organizations were ranked the least prepared.
By Matt Kapko • March 22, 2023 -
Ransomware gangs incite fear in victims to fuel attacks
Attacks involving data theft nearly doubled and harassment spiked 20 times by late 2022, Palo Alto Networks Unit 42 said.
By Matt Kapko • March 21, 2023 -
Security drives software purchases for half of US companies
The study from Capterra comes weeks after the U.S. rolled out plans to shift liability for weak product security onto the tech industry.
By David Jones • March 20, 2023 -
Global cybersecurity spending to top $219B this year: IDC
Persistent cyberattack threats, increased regulations and the demands of hybrid work are driving sustained growth.
By Matt Kapko • March 17, 2023 -
Cybersecurity market confronts potential consequences of banking crisis
Bank seizures impose new challenges on vendors in every segment and may spur consolidation.
By Matt Kapko • March 16, 2023 -
SVB turmoil could mean long-term uncertainty for enterprise IT
The demise of Silicon Valley Bank created a void in tech startup funding and raises questions about the health of the vendor ecosystem.
By Matt Ashare • March 14, 2023 -
Shift to secure-by-design must start at university level, CISA director says
Jen Easterly says secure coding and memory safety should be incorporated into computer science curriculum.
By David Jones • March 13, 2023