Strategy: Page 16
-
New York cyber lead warns of what states face in critical infrastructure defense
Government agencies and the private sector must work collaboratively to combat increasingly sophisticated threat activity, Colin Ahern said.
By David Jones • July 25, 2023 -
White House secures safety commitments from 7 AI companies
OpenAI, Microsoft and Google are among the companies committing to robust testing and investments in cybersecurity safeguards to defend AI models prior to release.
By Lindsey Wilkinson • July 21, 2023 -
 Explore the Trendline➔
Explore the Trendline➔
 .shock via Getty Images
.shock via Getty Images Trendline
TrendlineRisk Management
An esclation of cyber risks facing businesses and government has made cyber resilience a major priority.
By Cybersecurity Dive staff -
US government plays catchup on phishing-resistant MFA
Security tools have evolved to include more accessible protocols that meet stringent authentication requirements. The government wants to embrace that.
By Matt Kapko • July 20, 2023 -
Microsoft offers free security logs amid backlash from State Department hack
Federal officials and rivals blasted the company for charging customers for additional security features.
By David Jones • July 19, 2023 -
GoTo, parent company to LastPass, names new CISO
The change in security leadership comes months after the third-party cloud storage service GoTo shares with LastPass was breached.
By Matt Kapko • July 19, 2023 -
White House shares the 69 initiatives slated to shore up national cybersecurity
“If the strategy represents the president’s vision for the future, then this implementation plan is the roadmap to get there,” Acting National Cyber Director Kemba Walden said.
By Matt Kapko • July 13, 2023 -
Cybersecurity funding drops sharply in Q2
Seed funding rounds dominated, while the enterprise market continued a trend of consolidating security vendors.
By David Jones • July 11, 2023 -
JumpCloud abruptly initiates mass API key reset
The company did not specify the nature of the incident, but the sudden decision to reset all API keys could indicate something is amiss, one expert said.
By Matt Kapko • July 10, 2023 -
TPG to buy Forcepoint’s public sector cybersecurity business for $2.45B
The deal for Forcepoint’s government and critical infrastructure-focused business marks one of the largest in the cybersecurity market this year.
By Matt Kapko • July 10, 2023 -
Only 5% of CISOs report to CEOs, survey finds
CISOs are still most likely to report to the CIO, but Heidrick & Struggles expects that to change as cyber responsibilities evolve.
By Matt Kapko • July 7, 2023 -
IronNet in NYSE compliance crosshairs after failing to file quarterly earnings on time
Management at the cybersecurity firm has been in talks on a deal to raise additional capital and go private.
By David Jones • July 6, 2023 -
The role for AI in cybersecurity
Generative AI can become an ally for new security professionals who may otherwise feel overwhelmed. For more seasoned security analysts, it can offer time to refine their skills through automation of repetitive tasks.
By Sue Poremba • July 5, 2023 -
How bad code fuels security mishaps
Spotting code that messes up operations or hurts security requires a proactive approach — and direct insight from developers.
By Jen A. Miller • June 30, 2023 -
White House releases cyber budget priorities for fiscal year 2025
Federal agencies are advised to demonstrate how their spending aligns with the national cybersecurity strategy.
By Matt Kapko • June 29, 2023 -
What to do after a data breach
Long before a data breach, well-prepared companies set up incident response teams with workers from multiple departments.
By Sue Poremba • June 29, 2023 -
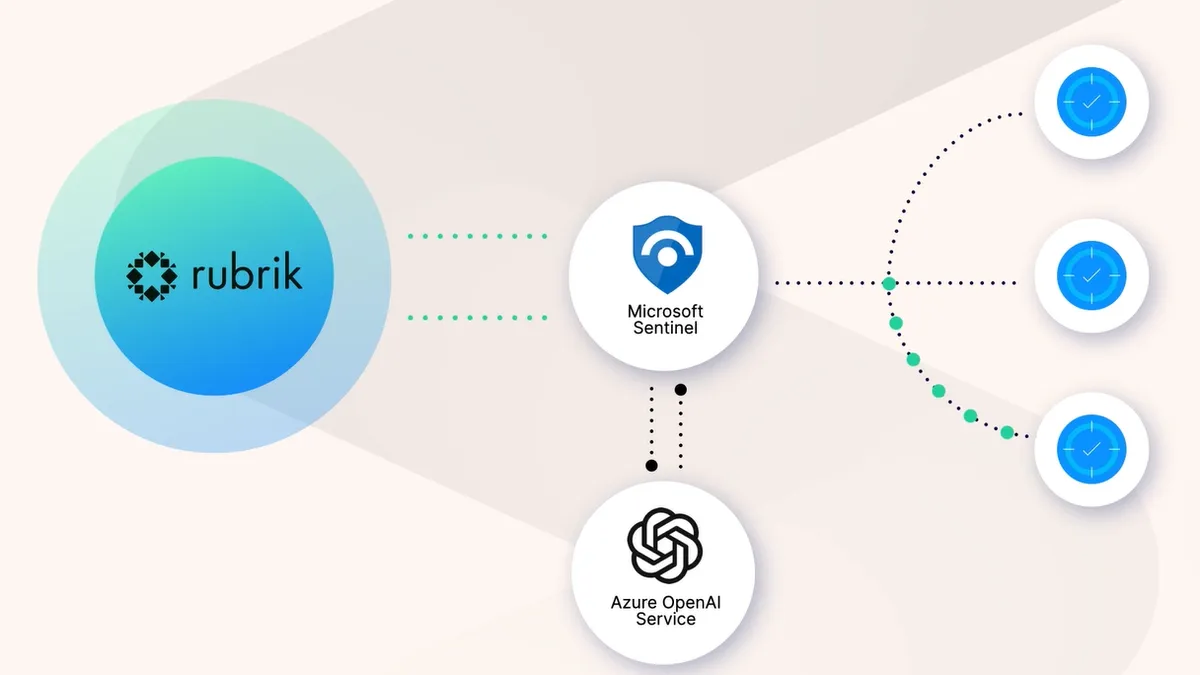
Rubrik, Microsoft partner to leverage generative AI for faster incident response
The collaboration will integrate Rubrik Security Cloud with Microsoft Sentinel and Azure OpenAI Service.
By David Jones • June 28, 2023 -

 jimmyweee. (2016). "Baltimore" [Photograph]. Retrieved from Flickr.
jimmyweee. (2016). "Baltimore" [Photograph]. Retrieved from Flickr.
State and local governments grapple to mitigate cyber risks
Municipalities are being pushed to step up investments amid high insurance premiums and strict demands on risk prevention.
By David Jones • June 27, 2023 -
How are states supporting K-12 cybersecurity amid growing threats?
As state efforts slowly ramp up to help struggling districts, they alone can’t completely remedy cybersecurity risks, one ed tech expert said.
By Anna Merod • June 23, 2023 -
Cyber CEOs are all-in on generative AI
Generative AI and LLMs are gaining attention in the security industry but not everyone is convinced the technologies will deliver the benefits promised.
By Matt Kapko • June 21, 2023 -
LastPass CEO reflects on lessons learned, regrets and moving forward from a cyberattack
Karim Toubba is ready to talk nearly a year after LastPass suffered a cyberattack that became one of the biggest security blunders of 2022.
By Matt Kapko • June 13, 2023 -
Cyber insurance market is stabilizing as growth remains certain, Moody’s says
Escalating price increases have moderated as the business has become profitable. Insurance firms are placing tight controls regarding cyber hygiene practices.
By David Jones • June 8, 2023 -
Dragos to slash 9% of workforce, trim other costs amid sales slowdown
The industrial cybersecurity specialist cited is reporting a longer sales cycle and is fighting to maintain long term independence.
By David Jones • June 8, 2023 -
Existing security policy for critical infrastructure needs major overhaul, commission says
The Cyberspace Solarium Commission 2.0 says the federal relationship with the private sector is based on outdated policy.
By David Jones • June 7, 2023 -
When adopting security tools, less is more, Gartner says
Security professionals say they want to consolidate vendors but, in actuality, Gartner fields far more calls about new technologies than reducing the cyber tech stack.
By Naomi Eide • June 6, 2023 -
CrowdStrike adds threat data to generative AI push
The security vendor plans to use different LLMs for specific purposes. It may also build some of its own, CEO George Kurtz said.
By Matt Kapko • June 1, 2023