Policy & Regulation: Page 4
-

 Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
CISA catalog falls short on CVEs targeted by Flax Typhoon
A report by VulnCheck highlights the ongoing backlog in identifying active exploitation of CVEs.
By David Jones • Sept. 24, 2024 -
Sponsored by Fortinet
Why it’s key to foster GenAI buy-in for SecOps
Generative AI is now one of the most effective ways to strengthen SecOps. Explore its potential.
Sept. 23, 2024 -
US authorities take down a Mirai-variant botnet tied to DDoS threat
An FBI-led operation to disrupt a China-linked botnet comes months after a similar operation in January linked to Volt Typhoon.
By David Jones • Sept. 19, 2024 -
Suffolk County ransomware attack linked to lack of planning, ignored warnings
A special report blames county officials for ignoring FBI warnings during the 2022 attack and an overall failure of IT and security leadership.
By David Jones • Sept. 18, 2024 -
Key cyber insurance stakeholders urge government to help close $900B in uncovered risk
Marsh McLennan and Zurich Insurance Group issued a white paper urging a public-private partnership to help tackle a growing coverage gap. The White House is working on a plan.
By David Jones • Sept. 6, 2024 -
White House launches cybersecurity hiring sprint to help fill 500,000 job openings
National Cyber Director Harry Coker Jr. unveiled the program as part of an effort to fill a continued gap in cyber, technology and AI positions.
By David Jones • Sept. 5, 2024 -
Prolific RansomHub engaged in attack spree, feds warn
The group has been among the most active threat groups of 2024, and is linked to a tool that can neutralize endpoint security.
By David Jones • Sept. 4, 2024 -

 Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
CISA launches cyber incident reporting portal to streamline breach disclosure
The secure portal is designed to encourage faster and more robust information sharing about malicious attacks and critical vulnerabilities.
By David Jones • Aug. 30, 2024 -
Automakers meet growing data privacy challenges, experts say
A Federal Trade Commission crackdown and lawsuit against GM show automakers are navigating legal risks.
By Michael Brady • Aug. 28, 2024 -

 Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
CISA officials credit Microsoft security log expansion for improved threat visibility
CISA officials say they plan to hold Microsoft accountable to ensure the company lives up to its commitments.
By David Jones • Aug. 27, 2024 -
SEC settles cyber case with Equiniti Trust as oversight questions linger
The firm, formerly known as American Stock Transfer, will pay $850,000 to settle civil fraud charges involving the theft of $6.6 million in client funds.
By David Jones • Aug. 26, 2024 -

 Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
CISA’s $524M headquarters slated for DHS campus in 2027
Construction for the agency’s centralized facility is expected to break ground in the fall. CISA staffers are currently spread out across five office rentals.
By Matt Kapko • Aug. 23, 2024 -
US, Australian authorities lead international push to adopt event logging
State-linked and criminal threat groups are using living-off-the-land techniques to hide their hacking activities behind regular security tools.
By David Jones • Aug. 22, 2024 -
White House details $11M plan to help secure open source
National Cyber Director Harry Coker Jr., speaking at Def Con in Las Vegas, says federal assistance must be bolstered by more ownership among the community.
By David Jones • Aug. 14, 2024 -
CISA director: Cybersecurity is ‘not an impossible problem’
In Jen Easterly's view, the solution to the industry's pains lies in secure by design. “We got ourselves into this, we have to get ourselves out,” she said during a media briefing at Black Hat.
By Matt Kapko • Aug. 13, 2024 -
Delta expects $380M revenue hit due to CrowdStrike outage
The company said it canceled 7,000 flights in five days due to the IT outage, according to a Thursday filing with the Securities and Exchange Commission.
By Roberto Torres • Aug. 9, 2024 -
Progress Software says SEC declines to pursue action related to MOVEit exploitation spree
The decision comes just weeks after a federal court dismissed most of the SEC’s civil fraud case against SolarWinds.
By David Jones • Aug. 8, 2024 -
Federal watchdog urges EPA to develop comprehensive cyber strategy to protect water systems
The report comes amid a rise in malicious cyberthreats from state-linked and criminal hackers targeting U.S. drinking water and water treatment facilities.
By David Jones • Aug. 6, 2024 -
CrowdStrike outage renews supply chain concerns, federal officials say
The White House and the U.S. Government Accountability Office are raising questions about the resilience of the software supply chain and memory safety vulnerabilities.
By David Jones • Aug. 2, 2024 -
SolarWinds legal ruling expected to narrow, but maintain SEC oversight on cyber transparency
The dismissal of most charges in a closely watched civil fraud case will test the ability of federal authorities to regulate risk disclosure.
By David Jones • July 29, 2024 -
CrowdStrike disruption direct losses to reach $5.4B for Fortune 500, study finds
A report from Parametrix estimates cyber insurance will cover only about 10% to 20% of losses.
By David Jones • July 25, 2024 -
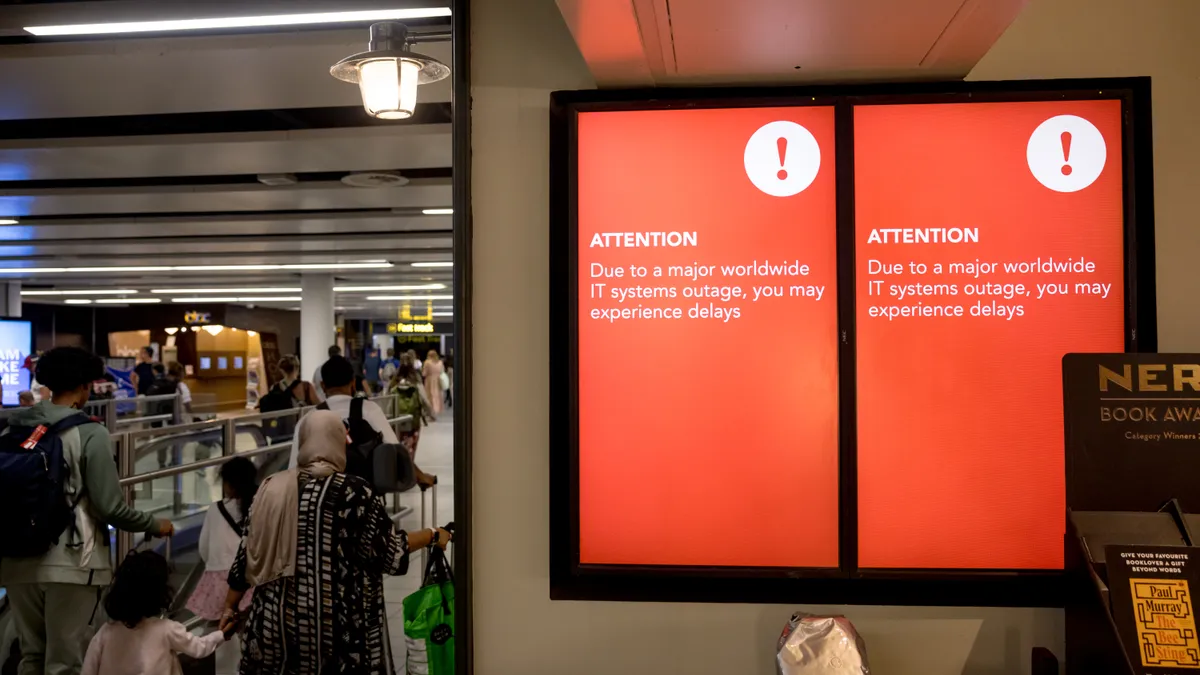
CrowdStrike, Microsoft scramble to contain fallout from global IT outage
Cybersecurity and IT experts said users are having major difficulties in recovery efforts, despite workarounds and guidance the vendors released.
By David Jones • July 22, 2024 -
Majority of SEC civil fraud case against SolarWinds dismissed, but core remains
The court ruling related to claims leading up to and immediately following the 2020 Sunburst supply chain hack.
By David Jones • Updated July 18, 2024 -

 Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
Photo illustration by Danielle Ternes/Cybersecurity Dive; photograph by yucelyilmaz via Getty Images
CISA calls for elimination of OS command injection vulnerabilities
Threat groups target vulnerabilities in widely used network devices. CISA’s latest advisory urges software makers to eliminate them at the source.
By Matt Kapko • July 11, 2024 -
MOVEit legal liabilities, expenses pile up for Progress Software
The prospective financial hit from a widely exploited vulnerability in the file-transfer service is growing. Progress confronts lawsuits, regulator scrutiny and government investigations.
By Matt Kapko • July 10, 2024