Cyberattacks: Page 30
-
25% of providers saw mortality rates rise after ransomware attacks, survey finds
This study of health delivery organizations is one of the first finding a direct impact on patient care. It comes roughly a year after a patient in Germany died as a result of delayed care following a ransomware attack.
By Rebecca Pifer • Sept. 27, 2021 -
Ripple effects from a cyber incident take a year to develop: report
Organizations are likely to both generate and suffer the downstream consequences of cyber incidents because of the technological reliance companies have on one another.
By Samantha Schwartz • Sept. 27, 2021 -
Ransomware compromises customer data in farm co-op attack
A Minnesota-based co-op became the second agricultural firm in recent days to be the target of ransomware, just weeks after the FBI and CISA warned of a wider threat to the industry.
By David Jones • Updated Sept. 24, 2021 -
BlackMatter gang targets Iowa agriculture cooperative in a test of critical infrastructure
Iowa-based New Cooperative, one of the largest grain suppliers in the state, is facing a demand to pay $5.9 million in ransom.
By David Jones • Sept. 21, 2021 -
What to know about software bill of materials
The Biden administration wants more transparency in the software supply chain. Will private industry join in?
By Samantha Schwartz • Sept. 20, 2021 -
Companies must develop operational plan for ransomware recovery
In the face of more frequent and sophisticated attacks, companies need to identify their most critical assets and work to limit cyberattack fallout.
By David Jones • Sept. 17, 2021 -
'Big game hunters': Ransomware groups target their perfect victim
Research from KELA found U.S. companies with upwards of $100 million in revenue are favored targets.
By Samantha Schwartz • Sept. 13, 2021 -
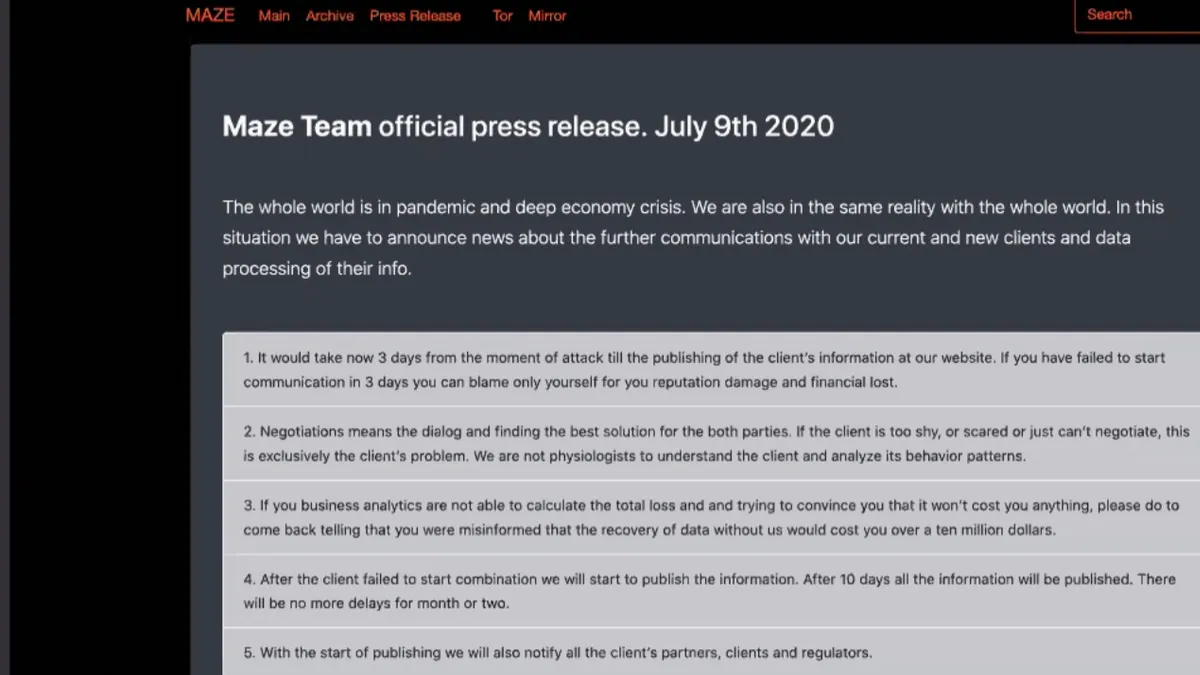
What ransomware negotiations look like
Fear can overwhelm the decision of whether to pay a ransom. But in negotiations, companies have to take a backseat.
By Samantha Schwartz • Sept. 9, 2021 -
What's at stake in a credential stuffing attack
Attackers gain a network foothold by using stolen credentials under the guise of an authenticated trusted employee or third party.
By Sue Poremba • Sept. 1, 2021 -
Why a ban on ransom payments will not work
Those most impacted by an attack are motivated to pay. In some cases, it's not the victim company but its customers who want service restored.
By Samantha Schwartz • Aug. 27, 2021 -
Should healthcare organizations pay to settle a ransomware attack?
The decision goes beyond finances: In healthcare, it's a moral judgement, too. "I don't think there's a single yes or no," said Michael Coates, former Twitter CISO.
By Rebecca Pifer • Aug. 13, 2021 -
Criminal middlemen administer access to privileged accounts
Ransomware attacks stem from a specialized division of labor selling stolen credentials and providing unauthorized access to the enterprise, according to an IntSights report.
By David Jones • Aug. 12, 2021 -
Researchers withholding vulnerabilities can create path to supply chain hacks
Bug bounty programs incentivize researchers to fully develop vulnerabilities by offering higher payouts. But that can create risk for the enterprise, Corellium's Matt Tait said.
By Samantha Schwartz • Aug. 5, 2021 -
Initial access brokers sell a way in, widening the ransomware market
The most popular network access points sold on the dark web offer insight for security teams to better understand what is most vulnerable to ransomware.
By Samantha Schwartz • Aug. 2, 2021 -
Ransomware, supply chain attacks put cyber insurers on notice
Malicious cyber activity will force the insurance industry to raise premiums, raise standards and, in some cases, negotiate ransom payments, newly released data from Coalition shows.
By David Jones • July 28, 2021 -
Pipeline operators raise concerns over aggressive TSA cybersecurity directives
Many of the agency's directives are rooted in basic cybersecurity hygiene, not necessarily lengthy digital transformation efforts, the TSA administrator said.
By Samantha Schwartz • July 28, 2021 -
OT cyberattacks could threaten human safety by 2025: Gartner
Critical infrastructure facilities are struggling to contain sophisticated malware and ransomware threats, Gartner research shows.
By David Jones • July 26, 2021 -
No ransom paid to obtain decryptor, Kaseya says
After consulting with experts, Kaseya said it decided not to negotiate with the criminals behind the attack.
By David Jones • Updated July 27, 2021 -

 Industry Dive/Cybersecurity Dive, data from Industry Dive
Industry Dive/Cybersecurity Dive, data from Industry Dive
How to keep business operations running after a cyber incident
While companies need to move quickly to mitigate the cyber event, they're also starting from behind. Once an incident happens, businesses have to catch up.
By Sue Poremba • July 23, 2021 -
White House ties cyberattacks to China, but private sector awaits stronger action
Security leaders urge more forceful action after the U.S. accused China of backing a campaign of malicious cyberattacks, including the early 2021 attacks against Microsoft Exchange server.
By David Jones • July 20, 2021 -
Kaseya restores SaaS monitoring service after REvil ransomware attack
The IT monitoring and management provider is working to restore service for on-premises customers after extensive hardening to protect against a future attack.
By David Jones • July 12, 2021 -
Kaseya: What's known (and unknown) about the ransomware attack
The historic ransomware attack against the remote-monitoring provider leaves a number of outstanding questions.
By David Jones • Updated July 12, 2021 -
Kaseya postpones service restoration, apologizes for attack
Outside engineers warned that Kaseya needs additional layers of protection as pre-existing vulnerabilities are revealed.
By David Jones • July 8, 2021 -
Kaseya misses first attempt to restore SaaS following REvil attack
The scope of the ransomware attack began to emerge, as thousands of SMBs and other organizations returned to work only to find systems compromised.
By David Jones • July 7, 2021 -
Kaseya wrestles with service restoration following supply chain attack
The company is working with federal officials to recover from a ransomware attack that Kaseya said impacted up to 1,500 downstream customers.
By David Jones • July 6, 2021