Dive Brief:
- Multiple Twilio employees were duped into providing their credentials to threat actors in a phishing campaign the communications platform described in a Sunday blog post as a “sophisticated social engineering attack.”
- The attackers gained access to some of Twilio’s internal systems that contain customer data on Aug. 4. The company declined to say how many employees were duped and the amount of customers potentially impacted, and said an investigation is ongoing.
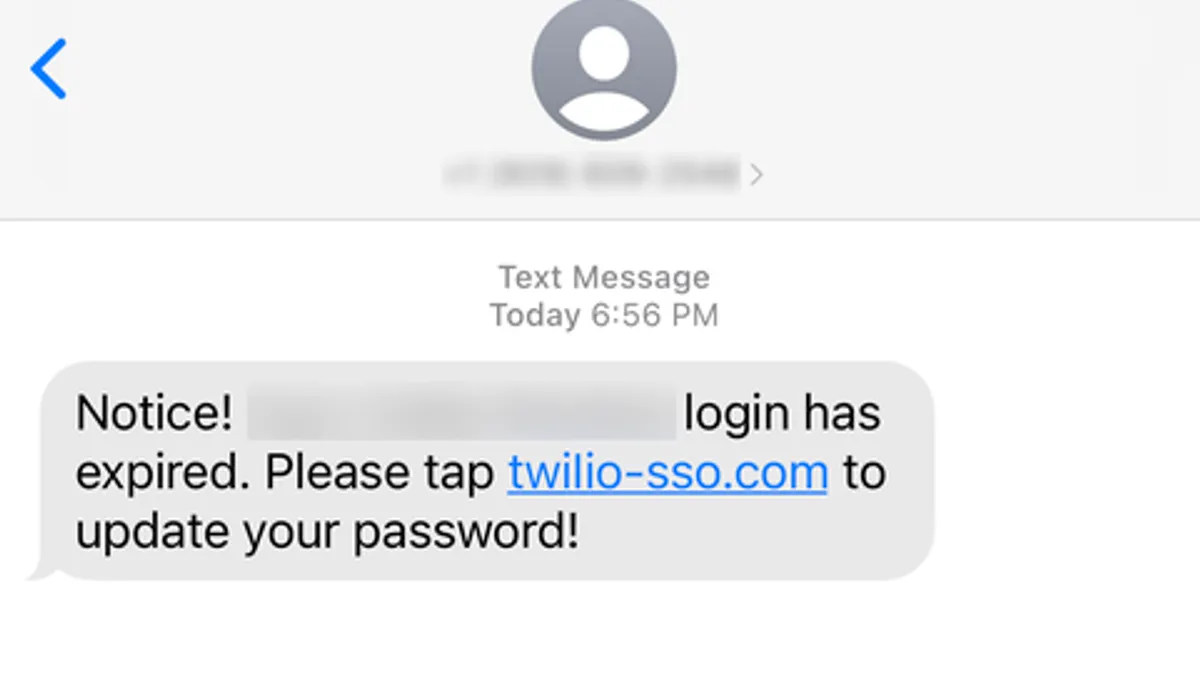
- The threat actors matched targeted employee names with their phone numbers to initiate the text message phishing campaign. Victims were tricked into updating passwords or changing their messaging schedule via spoofed URLs, according to Twilio.
Dive Insight:
Twilio was beaten at its own game. The platform’s application programming interface protocols are used by more than 275,000 customers to verify identity via two-factor authentication and engage customers in an automated manner.
Many of today’s most popular apps, including Facebook and Uber, use Twilio to communicate alerts and important updates to customers via text messages, voice and video. The carry-on effect of a threat actor accessing customer data could be significant if Twilio’s customers are later compromised.
The threat actors deceived some Twilio employees into sharing Okta credentials and two-factor authentication codes with spoofed URLs containing “Twilio,” “Okta” and “SSO” for single sign-on. Those links directed employees to a landing page impersonating Twilio’s sign-in page.
The company said current and former employees reported receiving the text messages, which purported to be from its IT department and originated on U.S. carrier networks.
Twilio said other organizations were subject to similar attacks and, despite a coordinated effort with network operators and hosting providers to stop the malicious messages and URLs, the threat actors resumed their attacks on other carriers and hosts.
“Based on these factors, we have reason to believe the threat actors are well organized, sophisticated and methodical in their actions,” Twilio said in a blog post.
The company asserted its use of modern and sophisticated threat detection and deterrence measures, which, Twilio said, makes the cyberattack notice especially painful. The threat actors behind the attacks have not yet been identified.
Twilio’s security team revoked access to compromised employee accounts after it discovered the attack, and the company said it’s notifying affected customers on an individual basis.