Dive Brief:
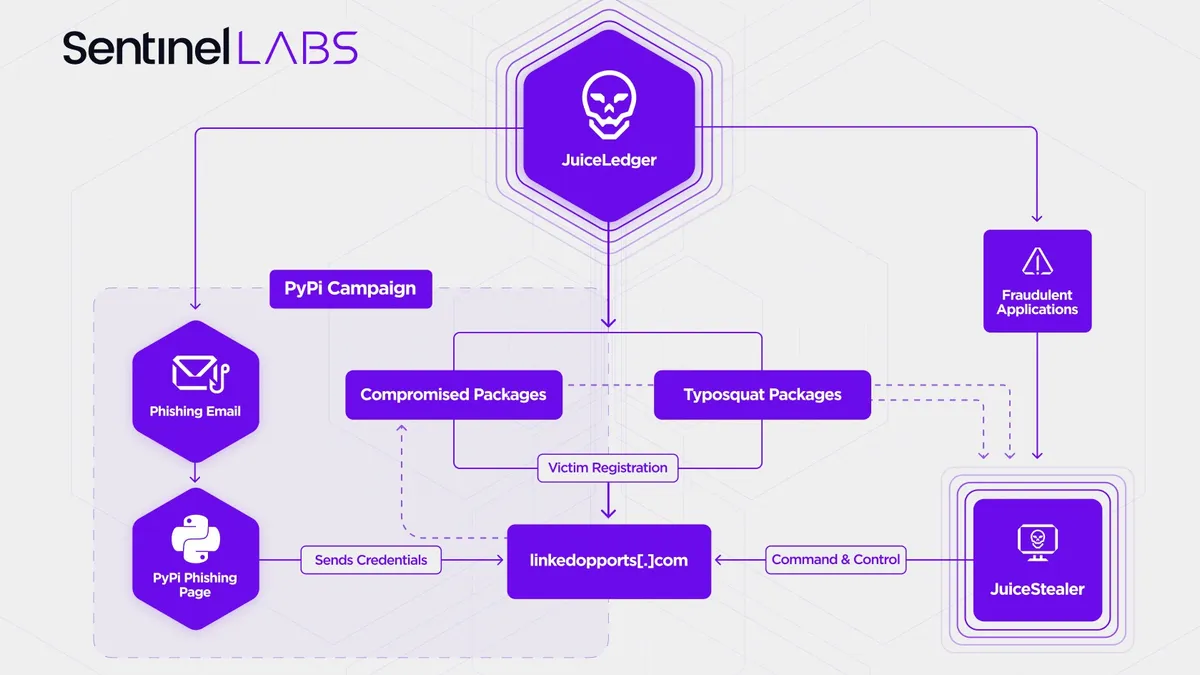
- A recently identified threat actor known as JuiceLedger has launched a series of supply chain attacks against Python Package Index (PyPI) contributors, marking the latest campaign against open source, according to researchers. The actor utilized a .NET application called JuiceStealer, designed to steal data from victim browsers.
- In late August, JuiceStealer operators were able to infect two legitimate PyPI packages with malware as part of a phishing campaign, researchers from SentinelOne and Checkmarx confirmed. Two packages with a combined total of about 700,000 downloads were compromised in the attacks.
- Researchers have identified hundreds of typosquatting packages delivering JuiceStealer malware.
Dive Insight:
JuiceLedger's attacks come at a time of heightened concern about the security of open source software.
Researchers from SentinelLabs in May investigated a supply-chain attack called CrateDepression, which targeted the Rust development community. The Rust Security Response Working Group issued an advisory about a malicious crate, called rustdecimal, which was used to deliver malware by typosquatting against rust_decimal.
The threat actor JuiceLedger was initially observed in early 2022 targeting potential victims with fake crypto trading apps, including a bot called the Tesla trading bot.
In late August, reports emerged about a phishing campaign against PyPI involving what was called a mandatory ‘validation’ process, which required a contributor to validate their package or face removal.
Users were directed to a fake site that mimicked the PyPI login page and then stole legitimate credentials entered onto the site.
“This campaign poses a new technique for attackers drawing close inspection of our research teams,” Tzachi “Zack” Zornstain, head of supply chain security at Checkmarx, said via email. “During the inception the finding of this attack correlated to previous data we had.’’
Because of the widespread use of open source in the enterprise, IT leaders and CISOs need to be cognizant of the potential risks of this supply chain attack on the security of their own systems, according to researchers.