Twilio employees aren’t the only individuals recently targeted by a sophisticated phishing attack.
Cloudflare on Tuesday said three employees fell for a phishing attack with very similar characteristics but, unlike Twilio, the content delivery network was able to thwart intrusion.
“This was a sophisticated attack targeting employees and systems in such a way that we believe most organizations would likely be breached,” Cloudflare CEO Matthew Prince wrote in a blog post authored alongside engineers Daniel Stinson-Diess and Sourov Zaman.
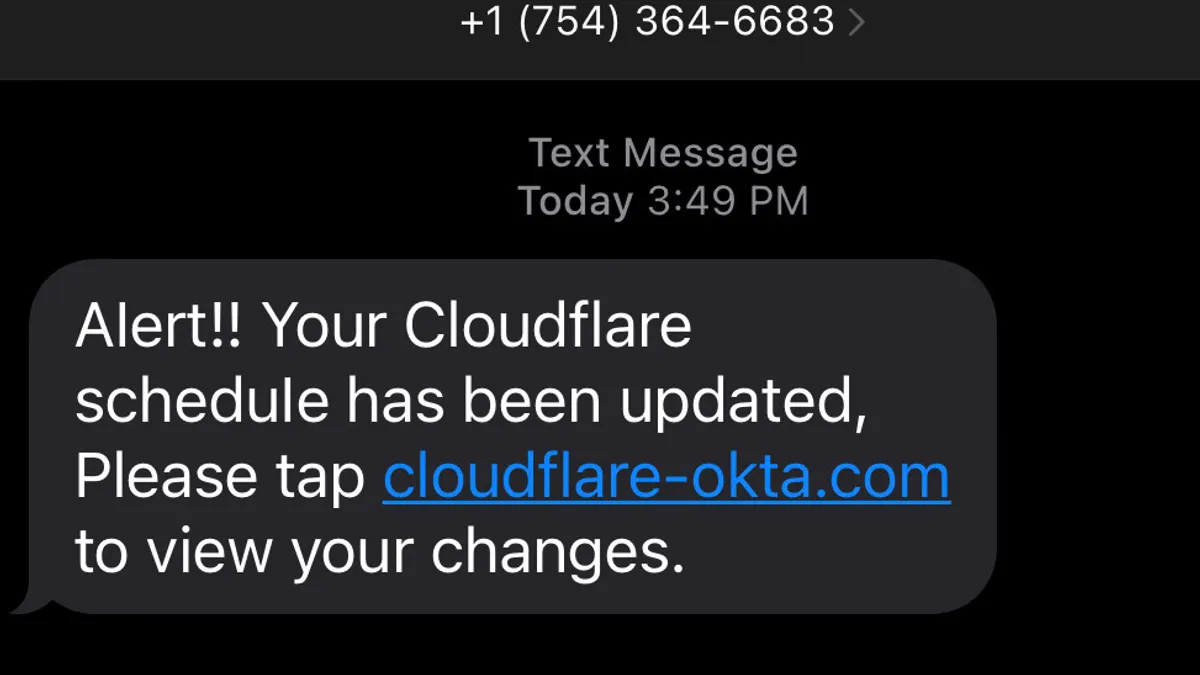
Cloudflare employees began receiving phishing text messages pointing to a spoofed Cloudflare Okta login page more than two weeks before Twilio employees were targeted with similar messages. At least 76 Cloudflare employees received text messages on their personal and work phones in less than a minute, the company said.
Some employees’ family members were targeted as well.
Cloudflare said it found no sign of compromise when it reviewed access logs to its employee directory, a detail that further illustrates a heightened level of advanced tactics and determination mobilized by the threat actors behind this attack.
All phishing text messages originated from four phone numbers issued by T-Mobile, and directed employees to a domain registered at Porkbun less than 40 minutes before the campaign began, Cloudflare said.
Attacks on third-party vendors such as Twilio and Cloudflare produce inherently greater risks because a breach could potentially compromise customer data, multiple analysts told Cybersecurity Dive.
The downstream impact of an attack, such as the one that occurred at Twilio, depends on what was compromised and when, Allie Mellen, senior analyst at Forrester, said via email.
Organizations, users and customers can all be at risk when employees unsuspectingly provide credentials to threat actors, granting access to internal systems and data.
The compromise of Twilio’s two-factor authentication adds another worrying wrinkle to that mix.
“Twilio’s actions can serve as an impetus for other organizations to proactively strengthen their two-factor authentication security safeguards and policies, as well as consider multi-factor authentication alternatives,” said Ron Westfall, senior analyst and research director at Futurum Research.
A tale of two responses
The divergence between Cloudflare and Twilio’s response to the phishing attack bears important lessons in transparency, resiliency and access.
While Twilio said its investigation remains underway, it has yet to disclose how many customers are potentially impacted, how many employees were tricked into providing their credentials and what type of customer data was exposed as a result of the attack.
Twilio’s customers need to react, but they can’t make appropriate moves without more detail about the extent to which their data might be compromised, said Frank Dickson, group VP at IDC. The company could be more forthcoming with a timeline for when those details will be shared, he added.
Discovering and remediating a breach is just one part of the process, which takes about one-fifth the time of a full assessment and shutdown of all compromised vectors, according to Dickson.
Absent further details, Twilio also faces questions about the resiliency of its authentication security practices, and the level of access granted when those controls fail.
Some systems should require more than two factors for authentication, but additional safeguards can be established with network architecture, Dickson said.
Segmenting access, implementing a zero-trust strategy and instituting least-privileged access controls can limit the blast radius following a breach, analysts said.
“Twilio needs to improve its response approach, especially since the company specializes in customer engagement software platform technology” and helps organizations meet some of their cybersecurity needs, Westfall said.
This incident should lead Twilio’s customers and partners to exercise greater caution in using the company’s products, he added. “This situation is not unique to Twilio, however the companies that have adopted a transparent and proactive approach have been able to restore a good degree of their brand integrity and trust in less time.”